CVE-2020-10107
Daily Expense Tracker System (DETS) is vulnerable to stored cross site scripting (XSS). This post will be a brief write up about discovery and exploitation of CVE-2020-10107. This vulnerability exists in the Daily Expense Tracker System project version 1, which you can download from phpgurukul, here.
According to phpgurukul’s website, this application has been downloaded at least 499 times – time of vulnerability discovery.
Discovering the Vulnerability
After a static code review, I noticed that SQL output is directly rendered to the user. I decoded to test whether there is input sanitation when storing values in the MySQL database. A simple payload as described below could be used when storing values in the MySQL database, to exploit the vulnerability when viewing manage-expense.php.
The php code below shows that values are grabbed directly from the MySQL database and are rendered to the user, without any output escaping.
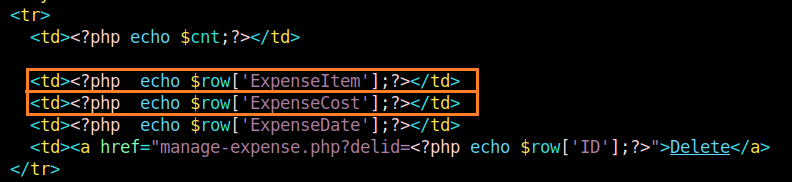
Verifying the Vulnerability
In the image below, it is seen that alert(1) and alert(2) are used. This is a habit which I have gotten myself into when testing for such a vulnerability. The numbers allow me to identify specifically which field is vulnerable. This is useful in cases where one field is vulnerable, but the other may not be.
<script>alert(1)</script> 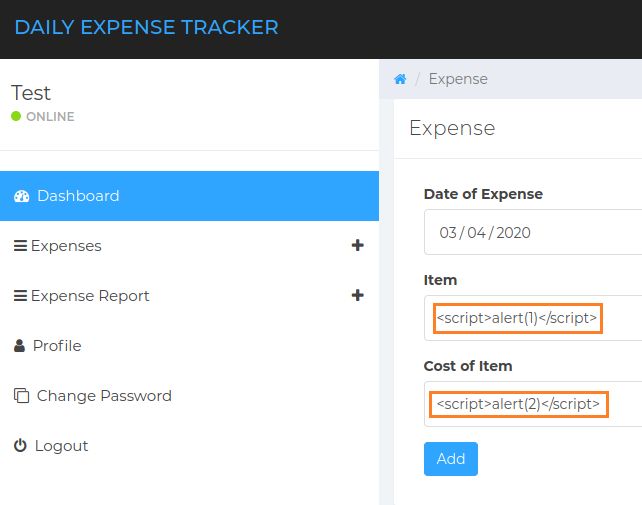
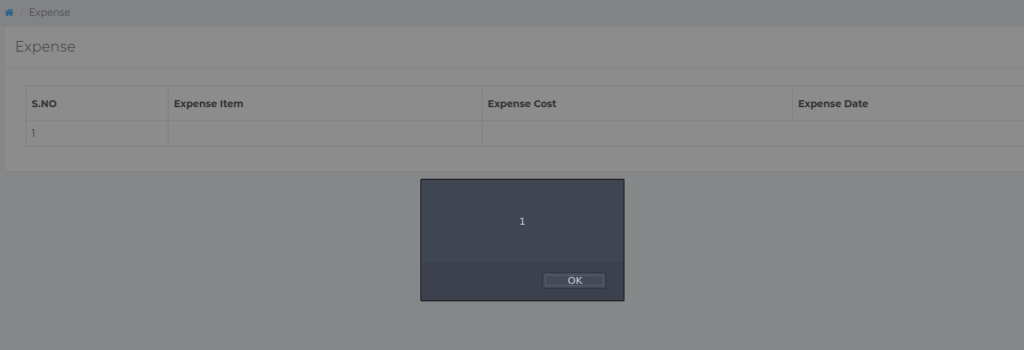
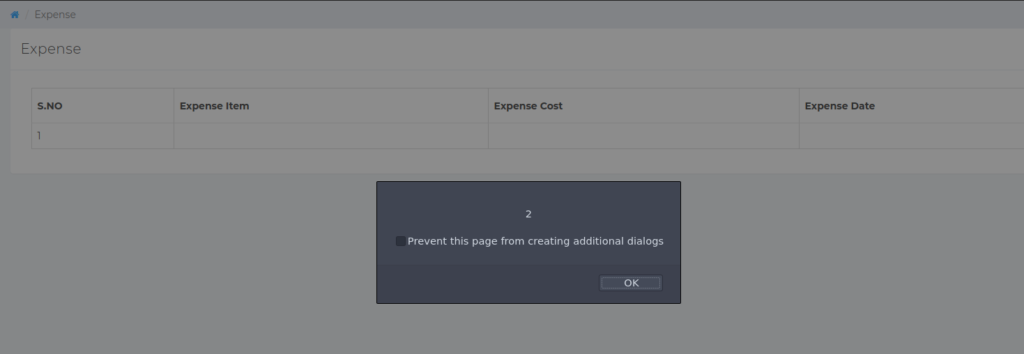
Thanks very useful. Will certainly share website with my good friends.
Super, happy to hear you found this useful 🙂
Good webpage you possess in here.